- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
All hands on deck: Attackers have entered the maritime industry
Not known to many is that the maritime industry is a popular target for state-sponsored cyber attackers. Yet, Hunt & Hackett has observed an increasing activity of Advanced Persistent Threat groups (APTs) in the maritime industry. In this series of blogs, here presented as one, the threat posed by APTs to maritime and related industries is analyzed and it is explained what motives lie behind their cyber-attacks.
Table of contents:
2. Most active attacking countries
1. Introduction & Challenges
The maritime industry is crucial to the global supply chain as well as the success of the ongoing globalization of the world’s economy. A large share of global trade is seaborne. Waterways connect the factories of China with the consumers in the West and vice versa. They enable the trade of oil from the Middle East to refineries all over the world. Without shipping, trade would severely slow down or even come to a halt, impacting consumer prices, the global economy and global wealth immediately. The oceans are of great importance for militaries as well. International waters can’t be claimed as territory and are free for anyone to access by law. For navies, such as the US Navy, the oceans play a vital role in strategically dispersing their military forces around the world in order to maintain their hegemony and surveil adversaries that could cause instability. The oceans also reduce dependencies on military bases of other nations as it enables them to get close to conflict situations on their own terms. Naval ships are equipped with the most advanced weapon-systems and navigation- and spy technologies to be able to operate far from home independently or in cooperation with other ships in a fleet.
Just like any other industry, the maritime industry is facing several challenges in the coming years. The COVID-19 pandemic has caused a small interruption in years of growth for the industry as a whole. The growth in the industry is a result of an increased global demand due to steep population and wealth growth. It is expected that the industry will soon recover fully from the effects of the pandemic and continue the trend of growth. Other, more structural challenges the maritime industry is facing, are industry 4.0, sustainability and resilience (see table 1).
| Industry 4.0 | Sustainability | Resilience |
| The maritime industry is undergoing a major transformation. The industry is progressively developing and applying technological advancements such as Big Data, Artificial Intelligence and Autonomy Technology. Information Technology (IT) and Operational Technology (OT) systems are increasingly being integrated for efficiency and effectivity purposes. Overall, maritime vessel are becoming more and more interconnected with processes on board and can be monitored and controlled from a distance. The downside is that it significantly increases both the attack surface and impact potential. | Currently, the maritime industry is responsible for around 2,5% of global greenhouse gas emissions. This number is expected to increase due to the foreseen growth of the industry. The International Maritime Organization (IMO) is actively promoting sustainability in the industry. An example of this is their goal of reducing CO2 emissions by 40% in 2030 and by 70% in 2050. International regulations to enforce sustainability in the maritime industry have already been implemented and the expectation is that more will follow. These environmental goals will drive a significant innovation push that will increase competition and impact the global competitive landscape. | The vulnerability of the global supply chain became exposed to the world when the merchant vessel ‘Ever Given’ got stuck in Suez Canal, blocking one of the most important waterways in the world. The incident, which lasted for only 6 days, costed an estimated amount of almost 10 billion US dollars. The blocking of the Suez Canal is just a stand-alone example, but clearly demonstrates that one local disruption works as a ripple effect and can severely impact the global supply chain. This incident is likely to have caught the attention of threat-actors, such as pirates, terrorist and cyber-ransomware groups on how to disrupt the global supply chain for their illicit actions. |
Table 1 – The current great challenges of the maritime industry explained.
Industry 4.0
All three of these challenges for the maritime industry have a link to cyber-security. The first, the transformation to industry 4.0 requires significant number of technological innovations, thus companies are heavily investing in Research & Development projects. However, these projects are time and capital consuming. This means that for countries like China, Russia and Iran, who are investing a lot of their resources in the upscaling of their maritime capabilities, lengthy R&D projects are not preferred. Upcoming economies, such as the BRIC (Brazil, Russia, India & China) countries, often fall behind when it comes to technological advancements. Western nations have been developing know-how and technologies on a top-notch level for decades, while the BRIC countries have only recently reached a competitive level. The catch-up with the West would take these countries many years and a fortune in research expenses. Gaining access to R&D information and technologies through cyber-attacks is cost effective and time efficient, particularly as there are currently limited consequences if one gets caught. Moreover, the nature of industry 4.0 is digitalized and interconnected. This opens a window for cyber-attackers to infiltrate systems and extract data from them, or even take over the control of ships entirely.
Figure 1 - The next phase of industralization: industry 4.0
Sustainability
The second challenge the industry is facing, is the quest for sustainability, one of the biggest challenges humanity is currently facing. In order to counter climate change and the global warming, an all-encompassing approach is needed. The global maritime industry can’t stay behind. Following directives and regulations from the IMO, the industry is moving towards lower greenhouse gas emissions, decreasing their negative impact on the environment. In order to achieve the ambitious goals of emission reduction, the maritime industry needs to be innovative. Efficiency needs to be boosted and materials used, need to be durable and sustainable. Adding to that, resources are getting scarcer, and energy needs to be renewable. These are demanding tasks for R&D departments. As stated before, R&D projects are costly and often take years before baring fruit. It will also change the competitive landscape where the new leaders will be the organizations that find the most (cost)effective solutions to reduce emissions. This means that the businesses competing in this space will want to keep a close eye on what the competition is doing. Additionally, when a country swiftly wants to comply with IMO regulations, without investing too much of its resources into sustainability innovations, keeping an eye on the developments in other countries is quite the logical move. However, innovative companies are often not eager to share their hard-won information or technological advantage. To still be able to obtain business secrets, some countries are likely to deploy their cyber-forces: APTs.
Resilience
The third major challenge the maritime industry is facing, is to uphold and improve the resilience of global trade system. As was quite painfully indicated by the ‘Suez incident’ in spring 2021, one incident along the trade pipeline has the ability to cause havoc worldwide. And yet again, cyberspace plays a vital role here. Ransomware can cripple entire companies, as happened with Maersk, the largest shipping company in the world with a market share of around 17%. One can imagine the impact of suddenly losing a key player in the industry on the global trade system. Regional and international ports have been targets in the past as well. The ports of Barcelona, San Diego, Rotterdam, Jawaharlal Nehru (India) are just a few examples of ports that have been under attack by hackers. These incidents have demonstrated the impact and therefore potential that threat-actors such as pirates, terrorists, cyber-ransomware groups and nation states can establish on the global supply chain through offensive cyber-operations. It has also highlighted how little is needed to cause major disruption in the global supply chain if one can control a ship at the right time and place.
In conclusion
It is clear that the maritime industry is undergoing significant change and is becoming an increasingly attractive target for hackers. This is further illustrated by Israeli cybersecurity firm Naval Dome, who have observed an increase of 900% in cyber-attacks on maritime operational technology (OT) between 2017 and 20201. For all companies active in or related to the maritime industry, this is plenty reason for concern. Hunt & Hackett defends its partners from cyber-threats by investigating who the threats are, why they are targeting this particular industry and how they plan on doing it. This is the reason why Hunt & Hackett tracks hacker-groups, often sponsored, backed or tolerated by nation-states and known as Advanced Persistent Threat groups (APTs) that have shown activity in the maritime- or related industries.
Hunt & Hackett does not just focus on the maritime industry to protect the maritime industry. Threat actors in related industries, such as industrial, manufacturing and technology, pose a long-term risk for the maritime industry, because they often depend on each other and develop innovations together. APTs active in related industries can easily jump over to maritime.
Currently, Hunt & Hackett is aware of 249 APTs active, now or in the past, in the maritime and related industries. In their effort, they have deployed 2.063 Tactics, Techniques and Procedures (TTPs) and 1.901 attacking Tools (see table 2). To describe these TTPs and Tools, how they work and when they are used would result in a book of considerable proportions. However, Hunt & Hackett carefully tracks these attacking methods and finds ways to defend against them, so you and your organization don’t have to.
| APTs | TTPs | Tools | |
| Maritime, Industrial, Manufacturing and Technology | 249 | 2063 | 1901 |
| Maritime, Industrial, Manufacturing | 116 | 1489 | 1399 |
| Maritime Industry | 76 | 1119 | 1096 |
Table 2 - The number of APTs, and the TTPs and Tools they used in agricultural and related industries as observed by Hunt & Hackett.
2. Most active attacking countries
Just as in agriculture (see the Hunt & Hackett series of blogs on agriculture), the usual suspects of offensive cyber-operations, being China, Russia, Iran and North Korea are very active in maritime- and related industries. There are a few notable differences though. Turkey and the United States are showing quite some interest in maritime and related industries, and Lebanon and Syria are also among the nations who are actively eagerly deploying APTs. In figure 2 it is shown which countries are the most active. Data collected by Hunt & Hackett shows that espionage and information theft are by a far the main objectives of the attacking APTs. What motivations lie behind these attacks? Hunt & Hackett has conducted an analysis on the most active nations. In the following part, China, Russia, Iran and North Korea are discussed. There is also some attention for the peculiar high ranking of Turkey and the United States.
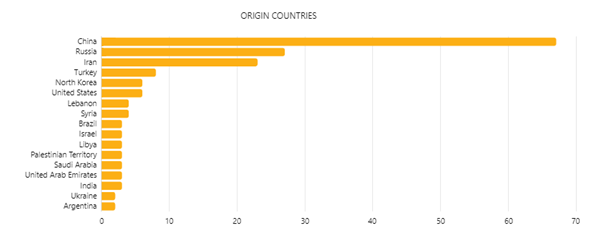
Figure 2 - Origin countries of APTs active in maritime- and related industries as observed by Hunt & Hackett.
China
When looking at the data, China is by far the worst offender and a threat to any innovating company in the maritime industry. A total of 67 APTs (now and in the past) operate from Chinese soil to obtain maritime secrets from companies and governments all over the world. This is no surprise, given the combination of three factors: (1) the inclusion of the maritime industry as a priority sector in China’s ‘Made in China 2025’ strategy, (2) China’s multipronged approach to obtain western technologies and innovations, which includes the use of illicit methods, and (3) China’s vast offensive cyber-capabilities.
“The most interest in our top industries is from China. [Through licit actions,] but also through illicit operations, that is by hacking. In particular directed at companies with high-tech knowledge. There’s a lot of interest in this ‘unique knowledge’. It just gets stolen.”
- Erik Akerboom, head of the General Intelligence and Security Service (AIVD) of the Netherlands (29-07-2021, EenVandaag)
Made in China 2025 is a strategy made to ensure China’s future place as world hegemony and the establishment of the most advanced and competitive economy in the world. The focus of the strategy is on high-tech manufacturing technologies. Maritime vessels and marine engineering equipment are specifically named in the strategy as key technologies. China also has a plan to obtain the technologies they desire. As shown in figure 3, the Chinese government has a multifaced system in place to acquire foreign technologies, a blend of licit and illicit methods of acquisition. Licit are the partnerships, mergers and joint ventures, but these often won’t get them to the most sensitive business information and most protected technologies. This is why they use the extensive capabilities of their intelligence apparatus. Through illicit ways, the Chinese government wants to get its hands on key technologies without going through lengthy and expensive R&D projects. China has a very large and capable cyber-force which is known to conduct espionage all over the world, often leading to frustrated Western countries who are struggling with a response China for its hostile acts because the intertangled relations and logistical and economic dependencies. Further complicating this issue is that involvement in cyber-attacks can often be easily denied.

Figure 3 – The multipronged approach of Chinese foreign technology acquisition efforts. Note the inclusion of the intelligence services in their approach.
To deal with the Chinese cyber-threat, it is important to understand how their APTs operate so their attacks can be countered. This is the reason Hunt & Hackett has tracked the Tactics, Techniques and Procedures (TTPs) and Tools that they have deployed in their attacks. Of the in total 249 APTs that have shown activity in maritime or related industries, 67 are attributed to China. In their efforts, they are currently using 650 TTPs and 675 Tools.
| Key stats on China: Maritime and Related Industries | |
| APTs | 67 |
| APT Names | APT1, APT10, APT12, APT14, APT15, APT16, APT17, APT18, APT19, APT2, APT20, APT21, APT22, APT23, APT26, APT27, APT3, APT31, APT4, APT40, APT41, APT5, AVIVORE, Blackgear, BlackTech, Blue Termite, Etc. |
| Level of Sophistication | High |
| Main Motives | Espionage; Information Theft |
| TTPs | 650 |
| Tools | 675 |
Table 3 - Key statistics on APTs originating from China, and the TTPs and Tools they use in the maritime and related industries as observed by Hunt & Hackett.
Russia
Only second to China, Russia is one of the most active nations when it comes to offensive cyber-operations in maritime and related industries. Russia’s cyber-force belongs to the absolute world top with a level of sophistication few countries can match. The Kremlin has not been reluctant to deploy its capable hacker groups to influence foreign decision-making, to destroy computer systems and to achieve economic gain. The maritime industry forms no exception: 27 Russian APTs have been observed to be active here with the purposes of espionage, information theft and financial gain.
Russia's main strategic goals relate to protecting its territory, maintaining its sovereignty, exploiting mineral and energy resources and improving quality of scientific research. The surrounding seas are of great importance to Russia because they hold a broad range of economic, political and military interests for the former Soviet nation. However, the merchant and military fleet of the Russians are outdated and are in need of modernization. Over the past few years, several maritime doctrines and strategy documents have been released in which Russia’s ambitions to modernize its maritime industry have been outlined. In 2019 the NATO Defense College assessed that Russia’s domestic capabilities are insufficient to successfully overcome their maritime modernization challenges2.
Luckily for Russia, they have other means to close the gap in their know-how and technologies. Nation-state sponsored APTs are often being used to infiltrate innovative maritime companies in order to extract intellectual property, documented know-how and technologies. Erik Akerboom, head of the general intelligence and security service of the Netherlands, said in an interview that Russia has been formerly known to be hunting for political information, but is now shifting their focus to acquiring Western technologies through cyber-operations3.
Hunt & Hackett is aware of the Russian threat and applies the method of Threat Modelling to counter it. When threat modelling it is vital to fully understand your adversary and its intentions. This is why Hunt & Hackett tracks down APTs and the tactics and tools they use. At this moment, Hunt & Hackett is aware of 27 Russian APTs that are or have been active in maritime and related industries. These 27 APTs have used 523 TTPs and 339 Tools in their efforts to conduct espionage, steal information or for financial gain.
| Key stats on Russia: Maritime and Related Industries | |
| APTs | 27 |
| APT Names | APT28, APT29, APT-C-34, Avalanche, Dungeon Spider, ELECTRUM, Gamaredon Group, Inception Framework, MONTY SPIDER, Operation BugDrop, Operation Domino, Operation Ghostwriter, Operation Windigo, Red October, RTM, Salty Spider, TeamSpy Crew, TEMP.Veles, Turla Group, UNC1878, UNC2452, White Bear, etc. |
| Level of Sophistication | High |
| Main Motives | Espionage; Information Theft; Financial Gain |
| TTPs | 523 |
| Tools | 339 |
Table 5 - Key statistics on APTs originating from Russia, and the TTPs and Tools they use in the maritime and related industries as observed by Hunt & Hackett.
The case of Turkey and the United States
Noteworthy are Turkey and the United States that appear high on the list of attacking nations in maritime and related industries. This is an anomaly compared to the threat landscape of other sectors such as agriculture, chemicals or energy. They appear in the list for a different reason than that of the other nations. Turkey has offensive cyber-capabilities but generally utilizes this capability to spy on other governments and dissidents. Why they appear high on the list is because they hack companies in the technology industry, an industry which Hunt & Hackett has identified as related to the maritime industry, to get access to the targets of their cyber-attacks. Evidence or explicit strategic motives lacks to be able to claim that they try to steal corporate secrets. For the US this appears to be the same case. They use technology companies to gain access to its initial targets, often governments. An example of this is the Belgacom hack, which the US conducted along with the UK, to spy on European political leaders.
Iran
For a long time in history, Iran’s ideals and culture dominated a large part of the Middle East. Home to one of the oldest civilizations of the world, Iran’s soil fostered a developed and prosperous people. In modern times, however, things took a turn for the worse. After first an Anglo-American coup in 1953 and the subsequent Islamic Revolution in 1979, Iran has struggled to meet its ambitions, which are fueled by the awareness of its rich history, to become a regional and international power once again. There are plenty of reasons why Iran is not succeeding in its idealistic mission. There is a lot of regional hostility, driven by religious reasons, but also by the threat of the Iranian nuclear program. These hostilities have resulted in numerous violent incidents, but have also motivated international sanctions, which are limiting Iran’s ability to meet its ambitions and have crushed the economy.
Part of Iran’s ambition of becoming a regional power is modernizing its commercial and military fleet4. Iran is abundant with resources and the best way to ship them is through the ocean. Once international sanctions are lifted, Iran could use its surrounding oceans to boost the economy and make the country prosper once again. In order to control the maritime industry, the Iranian regime founded the Iran Marine Fund (IMF) with the goal of aligning the maritime industry with Iran’s national interest. This highlights the value the regime assigns to its maritime capabilities. Adding to that, Iran needs a strong fleet to safeguard itself from foreign threats, such as archenemy Saudi Arabia, and to back its territorial claims in the Strait of Hormuz, Caspian Sea and the Persian Gulf.
Iran does not have the required knowledge, funds and technology within its borders to meet their high ambitions. To succeed, Iran must look beyond its borders. The international sanctions make it nearly impossible to find the resources they need in a legal way. This is why Iran has developed and encouraged state-sponsored hacker groups that could steal the technologies they need. Over the years, reports on Iranian APTs conducting espionage have seen a stark increase.
Hunt & Hackett has observed 23 APTs originating from Iran that have shown an interest in maritime and related industries at some point in time. In their efforts to steal intellectual property and foreign technologies, they have deployed 250 TTPs and 222 Tools. Hunt & Hackett tracks these APTs and their preferred ways of attacking to know what partners can expect when being attacked and how to defend from them.
| Variable | Key stats on Iran: Maritime and Related Industries |
| APTs | 23 |
| APT names | APT33, APT35, APT39, Bahamut, BlackOasis, Cadelle, Charming Kitten, CHRYSENE, Cutting Kitten, DNSpionage, Domestic Kitten, Fox Kitten, Group5, Infy, IRIDIUM, Madi, MuddyWater, Nazar, Rampant Kitten, Sima, Tortoiseshell, TRACER KITTEN |
| Level of sophistication | Medium |
| Main motives | Espionage; Information Theft |
| TTPs | 250 |
| Tools | 222 |
Table 6 - Key statistics on APTs originating from Iran, and the TTPs and Tools they use in the maritime and related industries as observed by Hunt & Hackett.
North Korea
North Korea is in somewhat the same position as Iran: great ambitions, even greater limitations. The communist country has focused on acquiring a nuclear arsenal and has had some success in its efforts. However, the nuclear program, along with neglect of human rights, has incited drastic international sanctions. Many nations have imposed sanctions on North Korea, ranging from the banning of luxury goods to the prohibition of conducting trade. North Korea has been trying to adapt to these unnatural challenges by setting up a global smuggling network. The most important way of smuggling much needed goods, but also to provide in the Supreme Leader’s luxurious needs, is through the seaways surrounding North Korea.
Whether working to smuggle coal, oil, luxury goods, or military equipment, North Korea’s maritime fleets have been a key component of Pyongyang’s sanctions evasion methods for years.
- Asia Maritime Transparency Initiative, 2021
The sanctions have made it impossible, however, for DPRK government and companies to acquire new ships or the know-how on how to build modern ships. Or at least, they should have. North Korea has been quite successful in its attempts to evade the international sanctions and has been getting its hands on ships. The latest success was only this year, when two oil tankers were added to the DPRK fleet. This shows that North Korea knows how to walk the illicit path and is not afraid to do so5.
Under Kim Jong-Un’s rule, North Korea has built a capable cyber-army with the intention of achieving its strategic goals illegally. These cyber-groups follow instructions from Pyongyang and perform cyber-attacks on financial institutions, companies in the technology industry and manufacturers. It is only logical that the North Koreans have set their eye on maritime industries as well, as waterways are so important to them.
Data gathered by Hunt & Hackett supports this last suspicion. Hunt & Hackett has observed 6 North Korean APTs to be active, now or in the past, in maritime and related industries. In their efforts, they have deployed 133 attacking techniques and 220 tools. Hunt & Hackett tracks these techniques and tools to keep its partners safe from North Korean espionage.
| Variable | Key stats on North Korea: Maritime and Related Industries |
| APTs | 6 |
| APT names | APT37, APT38, Kimsuky, Wassonite |
| Level of sophistication | High |
| Main motives | Espionage; Information Theft |
| TTPs | 133 |
| Tools | 220 |
Table 7 - Key statistics on APTs originating from North Korea, and the TTPs and Tools they use in the maritime and related industries as observed by Hunt & Hackett.
This concludes the writings on the attacking nations in the maritime industry. Below (table 8), a comparing recap of the four most active offensive countries can be found.
| Key stats of the four most active countries in attacking maritime and related industries | ||||
| China | Russia | Iran | North Korea | |
| Key strategic objective(s) | Catching up with western level of technology | Modernizing outdated merchant and military fleet | Modernizing outdated merchant and military fleet; enabling trade despite severe sanctions | Enabling trade despite severe sanctions |
| Level of cyber capabilities | High | High | Medium | High |
| Known motives for cyber deployment | Espionage; Information Theft | Espionage; Information Theft; Financial Gain | Espionage; Information Theft | Espionage; Information Theft |
| #APT groups | 67 | 27 | 23 | 6 |
| #TTPs | 650 | 523 | 250 | 133 |
| #Tools | 675 | 339 | 222 | 220 |
Table 8 - Overview of the most active attacking countries in maritime and related industries.
3. The Netherlands as a prime target
The Netherlands has a strong position in the maritime industry as one of the global leading nations. Centuries in buildup of know-how have resulted in a flourishing and world-renowned industry which resonates all over the globe. Companies such as Damen Shipyards, SBM Offshore, Huisman and Royal Boskalis are just a few examples of leading enterprises in global maritime industries. There are some terrains of expertise where there are few countries that are more developed than the Netherlands. This is because the maritime industry in the Netherlands has dedicated itself to the development of high-tech products since the 1980s.
This approach has been successful and has resulted in the dominance of the Netherlands in certain specialized parts of the maritime industry. An example of this is dredging, in which the Netherlands held a global share of 14,1% in 2009, only to see it grow to 36,1% in 2018. Also, Dutch shipbuilder Damen Shipyard has obtained a €5.5 billion contract for the construction of four German warships. These examples, even without mentioning the Port of Rotterdam, clearly demonstrate that the Netherlands’ expertise has resulted in a global frontrunner position.
According to a study conducted by MENON in 2018, the Netherlands especially excels in innovation related practices: ICT systems, knowledge creation and R&D. Noteworthy is that China and Russia, who are also included in the study, score particularly low on these three categories, meaning the Netherlands has a high comparative advantage over two countries notorious for their habit of (corporate) espionage and information theft. Not included in the study are Iran and North Korea, but it is not hard to imagine that the Netherlands has an even larger competitive advantage over them.

Figure 4 - Dutch tugs at work to get the Ever Given loose.
The development of high-tech products requires significant resources, which is a very capital and time-consuming process. Countries that are catching up to the level of sophistication some countries in the global West have already accomplished, often do not have the capital nor the willingness to await lengthy R&D projects. Yet, as they have a clear need to leapfrog the innovation cycle, they often prefer to hatch their bets and complement their own R&D efforts with an easier way, they choose the illicit path.
Through offensive cyber-operations, the offensive nations can get their hands on companies’ most valued and hard-earned trade secrets. Decades of investments and R&D projects that have secured an advantage not only over competing companies, but also over other nations entirely, can become lost to hackers. Therefore, it is vital that companies do not limit themselves by seeing cyber risks exclusively as an IT-issue. Organizations in the maritime sector need to protect themselves from these (advanced) attackers to protect their innovations and competitive advantage to ensure that they don’t lose their leading positions in the global maritime market.
So, what to do with this threat landscape information? Firstly, these industry specific blog-series are meant to raise awareness and educate organizations about their threat landscape. Secondly, the series aims to share some insights on how Hunt & Hackett goes about defending organizations against specific threats. This is the reason why Hunt & Hackett tracks APTs, their TTPs and Tools. In cybersecurity, this adversary-central approach is also known as Threat Modelling.
Hunt & Hackett works for innovative companies, in maritime and related industries, that invest a great deal in their R&D departments and want to keep their (trade)secrets just that: secrets. The approach we provide our customers with is data-driven, and focuses on the adversary: what attacking techniques do they apply and how can we defend from them? This is the reason why Hunt & Hackett tracks APTs, their TTPs and Tools.
Having an adversary-central approach, that is within the cybersecurity community also known as Threat Modelling, is required to make the threat landscape actionable. With this approach the Tactics, Techniques and Procedures (TTPs) and tools of a set of relevant adversaries form the basis to build-up the defenses of an organization. This specific threat picture can then be translated into specific security controls (e.g. CIS, NIST, ISO) and data-sources to log and actively monitor. How this can be done is outlined in some of our previous blogs:
- Threat Modelling as starting point;
- Applied Threat Diagnostics;
- Insights: the driving force behind a digital immune system.
Figure 5 – Hunt & Hackett has observed an increasing cyber-threat in maritime and related industries.
This concludes this Hunt & Hackett series of blogs on the increasing cyber-threat in the maritime and related industries are facing (see figure 5, which outlines the increase of APT activity over the years). Detection & response plays a key role in defending an organization against the maritime and related industries specific threat landscape. As not all MSSP/MDR offerings are equal, Hunt & Hackett has written an ‘Buyer's Guide to Managed Detection & Response (MDR)’ that can help organizations select a modern MDR-solution that best fits their needs.
4. Sources
- https://www.seanews.com.tr/maritime-cyber-attacks-soar-900pc-in-three-years-says-naval-dome/187618/
- https://www.ndc.nato.int/research/research.php?icode=574
- https://eenvandaag.avrotros.nl/item/aivd-topman-ziet-dreiging-toenemen-en-wil-meer-kunnen-doen-tegen-cyberaanvallen-we-moeten-sneller-slimmer-en-beter-zijn/
- http://www.idro.ir/en-us/Projects/Documents/Strategic%20Plan%20for%20Iranian%20Marine%20Industries.pdf
- https://amti.csis.org/north-korea-still-obtaining-new-oil-tankers-despite-sanctions/
- Data used in all tables and figures 2 & 5: Hunt & Hackett Threat Diagnostic Tool