Security Program
Gap Assessment (SPGA)
Data driven assessment of your cyber security threats, controls and risk.
You are busy protecting your organization, but against what exactly? Have you analyzed the latest threats that are applicable to your organization? Do you have visibility into the attack methods and tools of the adversaries and translated them into security controls? And if so, how are your security controls layered to prevent, detect & respond to these threats?
Our Security Program Gap Assessment (SPGA) provides detailed insights into your specific threat landscape as well as any potential security gaps to defend against this. Security Program Gap Assessments are pivotal for organizations to assure they become and remain resilient against the cyber threats that matter specifically to them, by analyzing all underlying components!
Why it matters
Only the relevant controls will make a difference
Understand
your threats
Overview of key
processes & critical assets
Identify gaps in
your security program
Make your security program actionable
Estimate budget,
resources and time
Structure your
security dialogue
The Challenge
Are you constantly working towards more and better controls, but lack insights into what type of attack methods these controls are effective against? Being compliant with security norms or best practices typically provides limited insight against what type of attack methods an organization is protected. To gain such insight, it is important to determine what your key business processes are and who would target those. What attackers target your sector and what is their modus operandi? The current threat landscape is a fast moving target which mandates frequent alignment between the threat landscape, your risks & risk appetite, your security program and the underlying security controls that you put in place.
We provide our Security Program Gap Assessment service to help you analyze available data within your organization in combination with our world class threat intelligence. Furthermore, we help you to understand the relation between threat actors, their attack methods/ tools and your security controls. We ultimately enhance the structuring of the current controls to improve your current state of security against applicable threat actors to your organization. These insights will aid the continuous adjustment of your security program to improve your resilience against modern cyber attacks and secure your most critical business assets.
What you'll get
- Overview of your external threat landscape that provides a threat model with the most prevalent TTPs that your organization faces.
- Internal controls assessment that provides a benchmark of how well your defenses work from an intelligence, prevention, detection and response point of view.
- Assessment to determine the efficacy of the current security program & roadmap (or setting up a security roadmap if none exist yet).
- Data driven feedback loop from threat modelling and gap assessment to your security program.
- Typically performed as a yearly assessment.
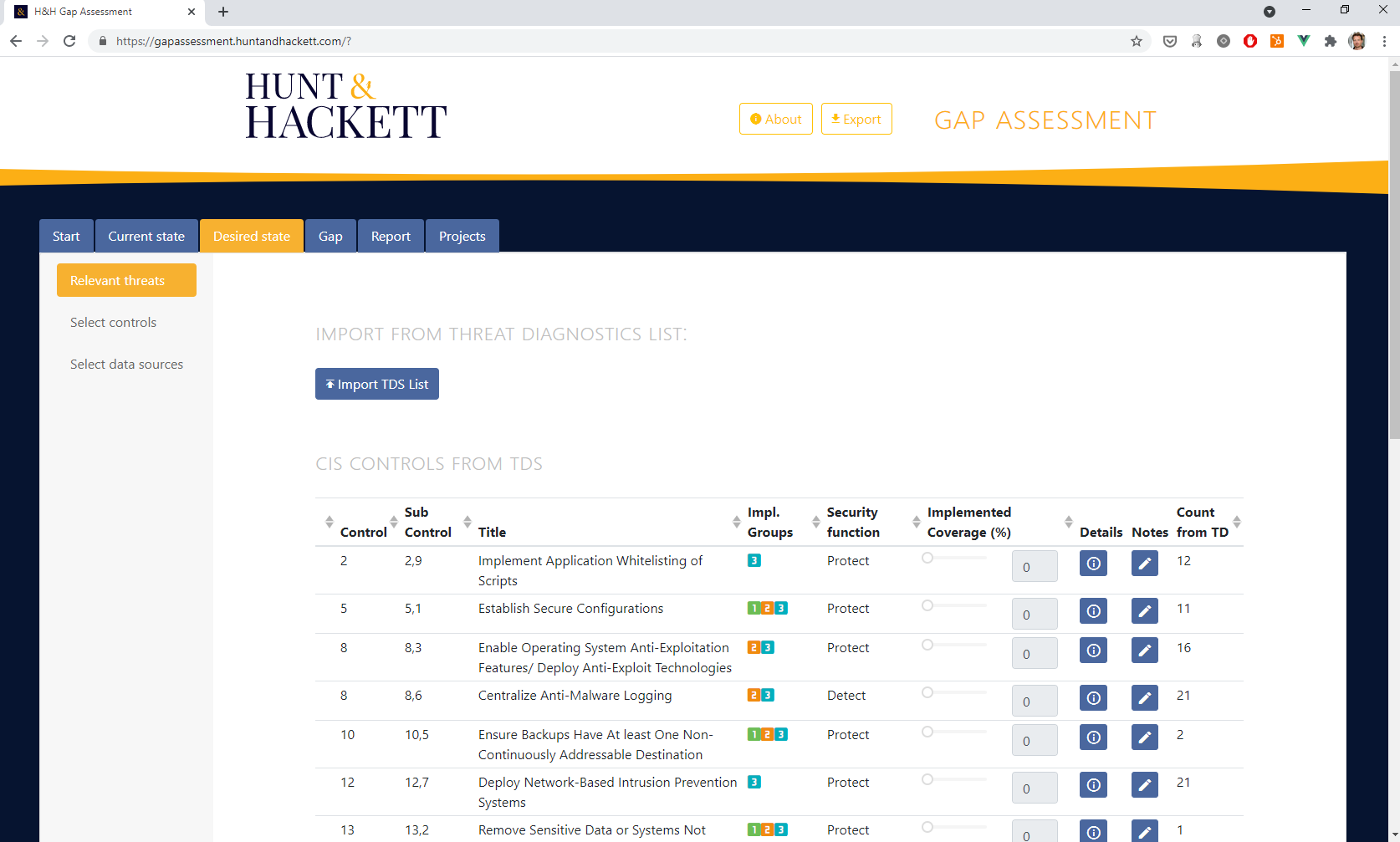
How it works
An overview of our Security Program Gap Analysis process
Intake
After you've contacted us, a Hunt & Hackett security expert will perform a short first triage and plan a threat diagnostics meeting together with you and your most knowledgeable colleagues on the business processes and available security controls.
Threat Diagnostics
Contracting
Based on the first threat diagnostics output a proposal is drafted (providing budget overview, technology to be deployed, hourly fees etc.). Additionally, a Mutual NDA and a Statement of Consent are provided.
Sign-off
You sign off on the Proposal, NDA and Statement of Consent and share the signed document with Hunt & Hackett. We will countersign those and start preparing for deployment.
Controls & Risk Assessment
Hunt & Hackett performs threat model research and conducts various interviews and technical analysis to assess controls in place to determine the current operation baseline.
Insights
Hunt & Hackett provides you with insights in:
- Threat model: data informed threat model for your organization. This maps out the relevant threat actors, their TTPs and how this affects your assets.
- Controls benchmark: assessment of the currently implemented controls. We believe that detection & response is very important and focus on detection coverage, in addition to preventative controls.
- Gap analysis: actionable report that prioritizes the most important actions between the current situation and the desired situation of your security program based on your specific threat landscape.
Closing the gaps
Together with you and based on our insights, Hunt & Hackett will create a cyber security roadmap to close the identified gaps. This roadmap will be actionable and consists of projects with cost indications that can be assigned to specific teams/people in your organisation.
Support
If needed Hunt & Hackett will continuously guide and support you during the implementation of the cyber security roadmap and reevaluate your security program periodically.
Why Hunt & Hackett?
Your trusted ally in cybersecurity
Skills & Expertise
The Hunt & Hackett team has unrivalled expertise and skills, having recruited the top experts from within the world of cybersecurity, incident response, forensics and operations to operate a SOC.
Methodology
Hunt & Hackett combines both expert analysis of historical forensic evidence and real-time threat detection and hunting, allowing the team to detect attacker activity.
Technology & Tools
The platform allows immediate, real-time visibility into your IT environment, identifying potential compromises and allowing quick action to make sure incidents don’t escalate.
Get in touch
Let’s outsmart your digital adversaries now