Managed Detection & Response (MDR)
Detect & hunt for evidence of attacker activity in your environment
Managed Detection and Response (MDR) encompasses the entire suite of activities performed to guard your security 24 hours per day, 7 days per week.
The service is delivered from our own Security Operations Center (SOC). Here, our experts combine threat intelligence, data-driven analytics and human expertise for the strongest detection and response strategies.
Based on the intelligent threat landscape of your own organization, we monitor each relevant data source (not just what’s relevant in general). This way we’ll help you to quickly outsmart any APT group targeting your assets and ramp up your resilience against ransomware, espionage and other cyber threats.
The Challenge
Monitoring is a continuous process, and only as good as your intelligence and talent.
- Navigating NIS2 compliance
The NIS2 Directive introduces strict cybersecurity standards across the EU, requiring organizations to enhance their cybersecurity with incident reporting, risk management, and continuous monitoring. This adds complexity, as businesses must not only protect against threats but also ensure compliance with evolving regulations—something many find challenging to manage effectively. - Threats go undetected for weeks
Most incidents go undetected for weeks (or even months), due to a lack of threat coverage or false positive alerts. However, if you want to reduce your risk, you need to be able to detect and respond in a matter of hours. -
Access to today’s threat intelligence
The biggest threats are posed by today’s vulnerabilities, not by what happened yesterday. Only if you avail over the latest threat intelligence, you can implement the right measures ‘just in time’.
-
The war for talent
High quality monitoring requires skilled analysts. That’s easier said than done in a world at war for this kind of talent. Remember: analysts thrive on handling incidents – so you’ll likely find the talent you need at expert organizations such as Hunt & Hackett.
The Benefits
Talented people, supported by innovative automation, take the detection of and response to cyberthreats out of your hands. Efficient and scalable.
- Increase resilience against ransomware, espionage and other threats
By investing in MDR, you will decrease the likelihood that serious cyber threats like ransomware will disrupt your business and organisation. -
Forensic & NIS2 readiness
Meet NIS2 requirements with comprehensive log retention and security telemetry, giving you full visibility and readiness for compliance audits. - Proactive threat detection & monitoring
We map threats to your specific data sources for precise monitoring, using an "assume breach" mindset to detect attackers already inside your network. -
Europe's most talented specialists
Our multidisciplinary, talented team of cybersecurity experts monitors your digital footprint day and night. They don’t shy away from an incident and are more than happy to work with you as ‘partners in crime’.
-
Leverages existing investments
Never let a good investment go to waste. Our open technology stack most likely supports your existing detection and response technologies. And if a piece of the puzzle is missing, we will advise on trusted solutions.
Our Approach
Our MDR service is all about building a continuous feedback loop that protects you against ever-changing attack patterns. Intelligence-driven automation plays a crucial role in our approach, to avoid the pitfall of playing a game of 'Whack-a-Mole' to stay in control. If you want to learn more about MDR in general, please have a look at The Definitive Guide to Managed Detection & Response (MDR).
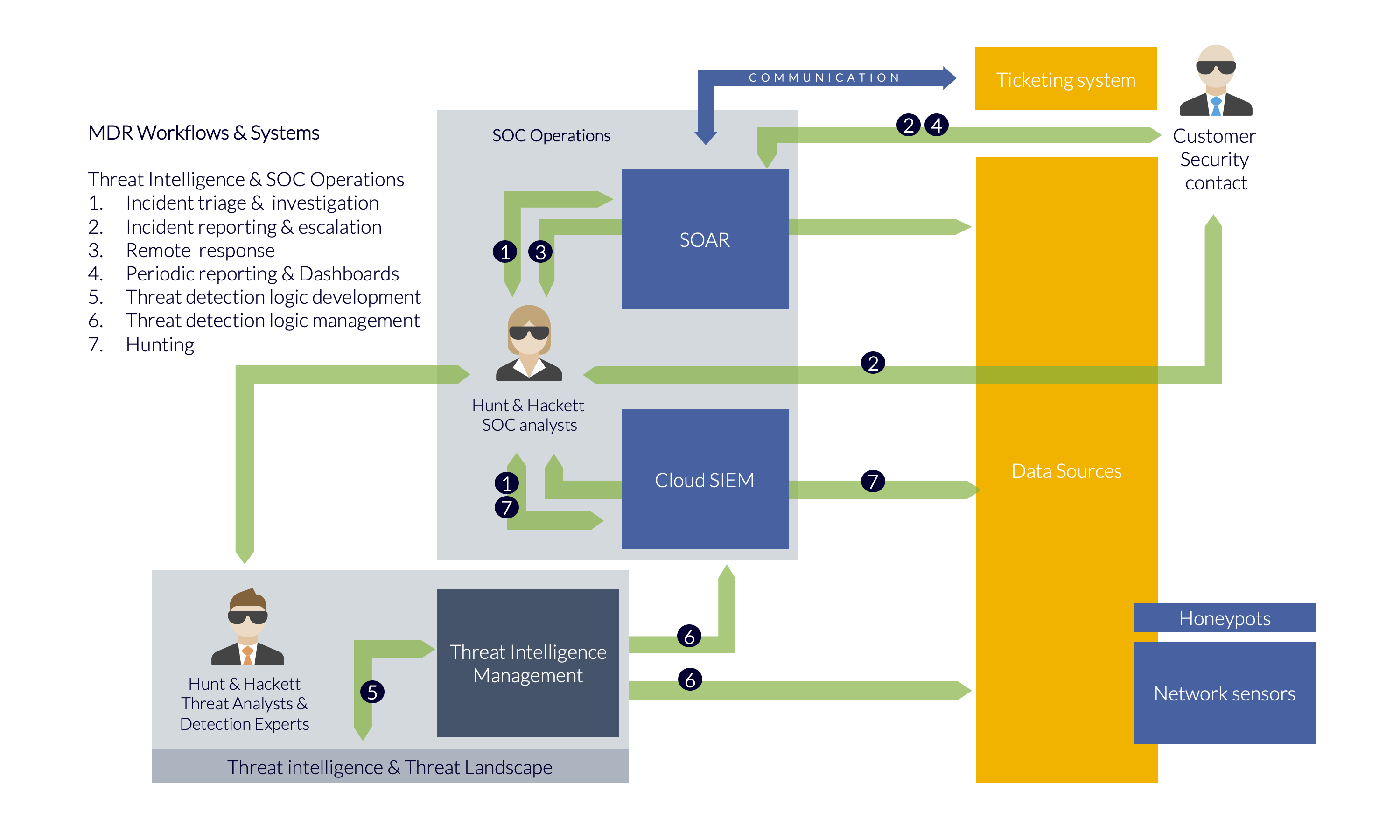
Our MDR platform as solid foundation
We store the security alerts and telemetry* created by your systems in our multi-tenant MDR platform. This platform is designed and built to support our innovative MDR-processes and incorporates trusted technologies such as SOAR (XSOAR), Next-Gen Security Analytics (Google Cloud SecOps) and anomaly detection systems.
Respond, hunt and optimize
Our analysts quickly respond (remotely if required) to incidents to ensure your organization remains in control. However, we don’t sit back and wait for new alerts. On the contrary: we hunt proactively for new threats and update the detection logic of your systems accordingly.
Insights and communication via app and portal
Our customers can contact our analysts, access the security overview and review incidents via our app or our portal.
The next step: Breach & Attack Simulation (BAS)
Once all your systems and processes for MDR are in place, it’s time to further mature your cybersecurity strategies with our Breach & Attack (BAS) services.
* We are technology agnostic and support a broad set of ‘sensors’, including:
- Network: network traffic inspection (ids, ngfw)
- Logs: server and application logs
- Cloud: Azure, Microsoft365 security logs
- Endpoint: Microsoft Defender ATP, LimaCharlie, ESET
If required we advise you on selecting one that’s right for you.
Tailored dashboards
for MDR customers
In addition to the core MDR service, we provide tailored security insights through real-time dashboards using the data already collected in our SIEM. These dashboards provide an additional layer of visibility into customers' environments, showing exactly what’s being logged, where the gaps are, and highlighting legacy protocols or misconfigurations which pose security risks. This enables you to prioritize security improvements in a data-driven manner and proactively address widespread, low-visibility issues. Watch the video below to learn more.
Why Hunt & Hackett?
Your trusted ally in cybersecurity
Skills & Expertise
The Hunt & Hackett team has unrivalled expertise and skills, having recruited the top experts from within the world of cybersecurity, incident response, forensics and operations to operate a SOC.
Methodology
Hunt & Hackett combines both expert analysis of historical forensic evidence and real-time threat detection and hunting, allowing the team to detect attacker activity.
Technology & Tools
The platform allows immediate, real-time visibility into your IT environment, identifying potential compromises and allowing quick action to make sure incidents don’t escalate.
Get in touch
Let’s outsmart your digital adversaries now
