- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Insights: the driving force behind a digital immune system
Krijn de Mik
@
Apr 16, 2021 2:40:40 PM
There is a staggering amount of data available in the field of cyber security today. A few short years ago this was unimaginable, yet, the whole the industry still operates on too few insights derived from this data. This needs to change.
Cyber resilience of an organization requires a data-driven defense strategy that is translated in a technical solution that is sophisticated enough to act as the digital immune system to your IT environment. Like your own immune system, a digital immune system is adaptable and constantly evolving. It is important that this system is able to deal with unknown attacks. As in the physical world, once a virus is beaten, it would be able to deal with the same type of attack again, and again. But a system that doesn’t evolve wouldn’t be able to deal with new types of threats. If your digital immune system does not adapt to mutations, it will quickly become ineffective and obsolete Such a system requires SOCs to transition from focusing on using static IOC’s as detection logic towards more abstract means for detection on a TTP level. This for example involves detection logic like machine learning algorithms, behavioral detection models and the use of rules that model behavior, like Sigma & YARA-L.
Prevention, detection and response is a complex, ever evolving set of activities, that require many different components to work together and be frequently (re)aligned. We believe in a systems-thinking approach to cyber security. We focus on the way that a system's constituent parts interrelate and work together as a system to form the overall solution. This approach leads to more effective solutions than when technology is applied in isolation. When the systems-thinking approach is complemented with data, intelligence from frontline experts and data-science techniques, it can create meaningful insights that guide the design of our solutions and technology. This data-science led approach enables you to address ever-evolving threats and tactics to by adopting your defenses and optimize your overall cyber resilience.
The components of the digital immune system
So, what are some of the components that should be part of a healthy digital immune system?
- Threat modeling: know what you are up against by determining your threat landscape and understand who is targeting you as an organization and how they operate. Without such insight any approach to defending and resilience it is opportunistic at best. See our blog on threat modeling for more details.
- Detection and Response: The outcome of your threat model dictates your mix of security controls: the security controls and technology to use for prevention, detection and response. It determines the data sources to be ingested by the detection and response technology and the detection logic that should be applied in order to detect the modus operandi of the relevant set of threat actors to your organization. See our blog on applied threat diagnostics for more details. This means that if for example APT28 (Russian State actor) is part of your threat landscape, data sources like ‘PowerShell logs’ and collecting ‘Process command-line parameters’ are vital for your detection. Occasionally Mimikatz is deployed by APT28 to collect credentials and obtain higher privileges in an infrastructure. Meaning that if you monitor these two types of logfiles, for specific command line parameters, you could detect APT28 activity in your network.
- Validation: Once you have identified your threat landscape and once you have the corresponding controls in place, it’s time to validate. Not once, but continuously. Is the immune system still healthy and operating as expected? Are there any weak spots that require supplements? See our blog on validation for more details.
These components need to constantly be (re)aligned with your threat landscape in order to be effective. They change constantly in volume, shape and form, depending on your threat landscape, IT environment, vulnerabilities, exploits and more. Your immune system needs to be able to adapt to new situations and needs to be capable of applying the most effective techniques towards detection and response. Sadly, this is not the norm today, yet it is essential to take into consideration when developing prevention, detection and response strategies that will last.
Insights as the driving force behind the digital immune system
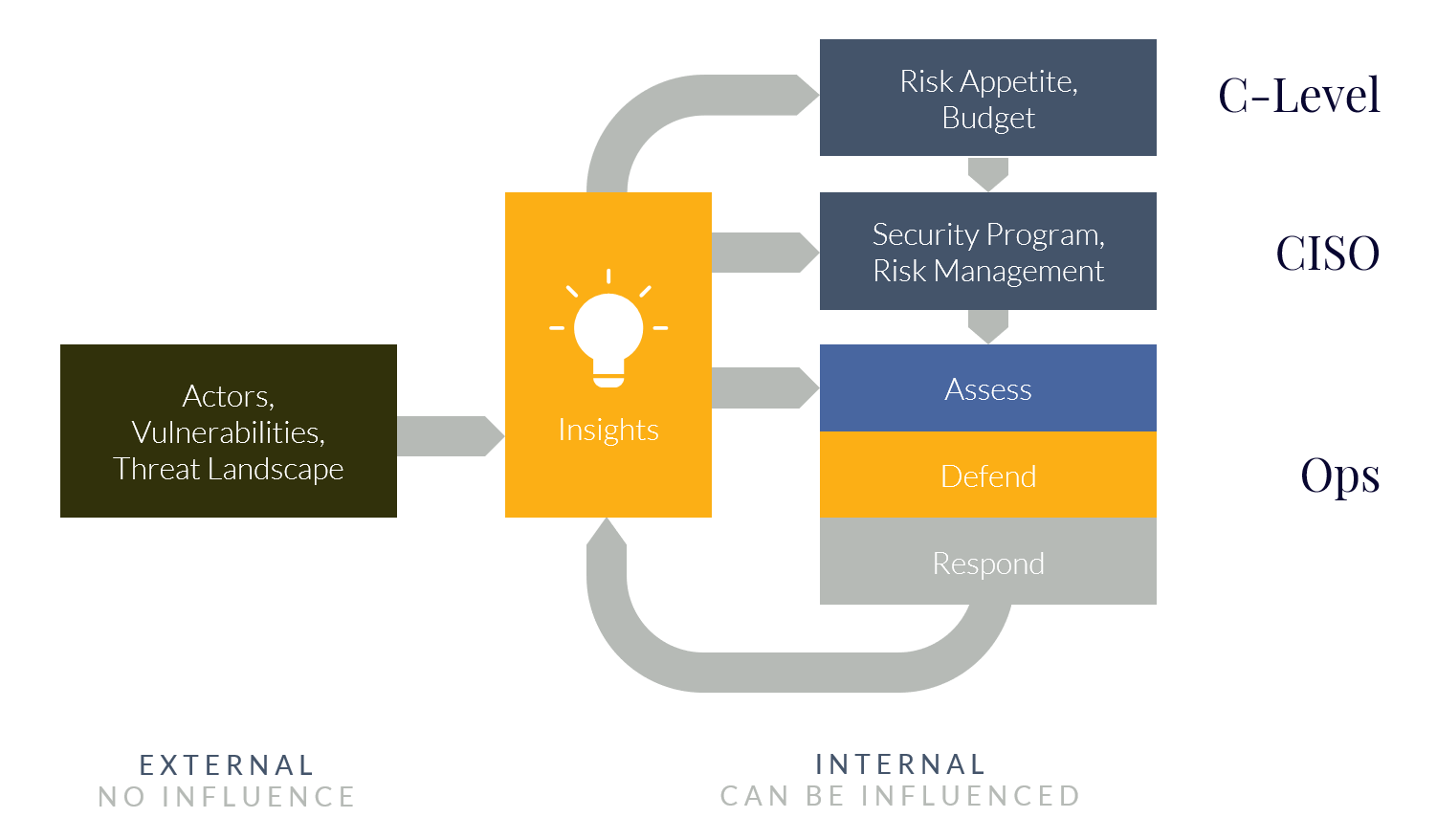
Data driven and actionable insights are key to a successful digital immune system. These insights link together otherwise isolated data and puts in in the right context for the audience. The insights are based on two categories of inputs:
- External threat intelligence: a change in the threat landscape may require a response to the immune system. Changes include newly discovered vulnerabilities (such as with Solarwinds, Exchange or activities from a group like SilverFish…) changes in attack methods (groups like EvilCorp refraining from using Dridex, but instead use drive-by downloads to get an initial foothold) and updated threat actor intelligence;
- Results from operational security: when detection capabilities detect a (potential) new incident through the Security Operations Center (SOC), or a Breach & Attack Simulation (BAS) run highlights a new vulnerability in the chain of security controls, it provides a key insight that should be used to adjust and improve the overall defense system.
These insights, once combined, will not only determine the best course of action, but they will form the feedback loops by which the system is constantly fine-tuned and improved where necessary. Some solicit a large response from all involved parties, while others require almost no action. The key here is to suggest the appropriate response to the right audience in the right context and appropriately timed. In most organizations there are three main roles that effectuate the security policy and benefit from insights:
- C-Level: has a need for insights to be put in a business context and drive changes to risk appetite and budget. The C-Level is ultimately responsible for the cyber security risks and need to understand their options. Insights support the understanding of the threat landscape, the current state of security in the organization and the resulting risk-exposure at the C-Level;
- CISO: has a need for insights to build organizational resilience by driving the security program and optimizing controls to manage security risks. The CISO can adjust course to address trends instead of incidents. The insights inform the CISO on the efficacy of the security program and allow them to adopt a more agile approach. The insights are also key for a CISO to communicate effectively with both the C-level as with the operations / technical people;
- Operations: The insights ensure a more tightly integrated execution of security operations. Typically, these teams are siloed, yet they thrive if they can freely share data. With the right insights the operations team has the context to understand what is going on and how it can affect the organization.
Immune system in action
To illustrate the immune system in action, here are some examples:
- An incident from Managed Detection & Response influences security program priorities to address trends instead of incidents;
- Breach & Attack Simulation creates feedback loops on how well prevention & detection controls are working, directly influencing the implementation of security controls and security program to align with risk appetite and threat actors;
- Red Teams provide insight into how advanced attack groups approaches your organization validates the security program and risk appetite are aligned to prevent successful similar attacks;
- Results from a threat model workshop highlight the current threat landscape and influences priorities in security controls and (possibly) budget;
- Emerging threat intelligence is applied to detection systems to improve threat coverage;
- A new vulnerability affects your security. Mitigating controls are quickly taken based on business risk exposure;
- Incident Response operational feedback loops ensure that investigation findings are quickly used to update preventative controls.
Get started with your own digital immune system
To get started with your own digital immune system, it is advisable to start small, improve and extend. For example, start with tracking relevant vulnerability news, see how it applies to your organization and what the next step should be. Then extend this for example to include the operational output of a Managed Detection & Response (MDR) service, from your own SOC, or from attack simulation outcomes.
If you want, Hunt & Hackett can operate a digital immune system for you as part of the Managed Detect & Response Service. We can augment or replace your security office by our multidisciplinary team of experts. Furthermore, if important components are missing in your digital immune system, be it threat modelling, detection & response, or validating, we can help to implement and manage it. Additionally, we can help you to extract information from your current information streams/sources and translate this into meaningful insights, making it a driving force for your digital immune system.