- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Threat Modelling as starting point
Know thy enemy and know yourself; in a hundred battles, you will never be defeated.
As a CISO of a mature organization, you have worked hard on building a security strategy, securing reasonable budgets, and the implementation of a range of security controls. Most likely you will have ensured your organization is compliant with the various security standards. Unfortunately, even with a maturing cybersecurity strategy it remains difficult to verify if your security operations, and the controls you’ve implemented, are truly capable of protecting your organization's assets.
Whether this is the case, depends largely on the threat landscape your organization is facing. After all, even Advanced Persistent Threat (APT) actors have their preferences. If your organization is known to be active in an industry of interest to APT-actor groups, such as life sciences, technology or manufacturing, CISOs face an immensely challenging threat landscape. The only way to win this battle is to understand who and what you are facing. Who are your adversaries? What are they after? What are their preferred methods of attack? Or, as the ancient Chinese general Sun Tzu once said: "Know thy enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle." In our world of cybersecurity we call this approach ‘Threat Modelling’. This approach is adversary-driven and at the heart of how we at Hunt & Hackett enable CISOs around Europe to outsmart their digital adversaries.
‘Knowing thy enemy’ requires intelligence and threat actor data
Threat Modelling as an approach to cyber security requires in-depth intelligence and threat actor data on all known and relevant actor groups that have an interest in your industry. This data is then aggregated and analysed to determine how this affects your organization and assets. A lot of this intelligence and data is publicly available. You will be able to find out which threat actor groups are most prominent. You can learn more about the tools they use, and their attack patterns. Even information about how to mitigate those attacks with security controls is publicly available. However, all this information is extremely fragmented, and changes quickly, which makes it hard to translate all this information into meaningful insights for your specific situation.
Some recent initiatives in the security sector can help your organization with the assessment of the treat landscape:
-
Threat actor data is increasingly being shared. Either as public data sets or as commercial feeds;
-
Threat actor tools and behavior are captured in a shared vocabulary, making much easier to compare different sources. The MITRE ATT&CK [1] framework is a key initiative here. Industries and geographies can be identified in a uniform way;
-
Defense frameworks are maturing (CIS Controls [2], NIST 800-53 [3], ISO 27002 [4]), providing baselines for best practices.
Yet even with these developments it still remains difficult for individual organizations to truly understand their adversaries, their motivations and their methods. That’s where Hunt & Hackett comes in.
A unique tool for Threat Diagnostics
Using the initiatives mentioned above, and the years of experience of our team, Hunt & Hackett has developed an advanced threat diagnostic tool that helps to prioritize the required steps to make organizations more secure. The tool identifies the relevant threat actors your organization is facing, given the industry and countries you operate in, and then maps the Tactics, Techniques and Procedures (TTPs) used by these APT actors to your defenses.
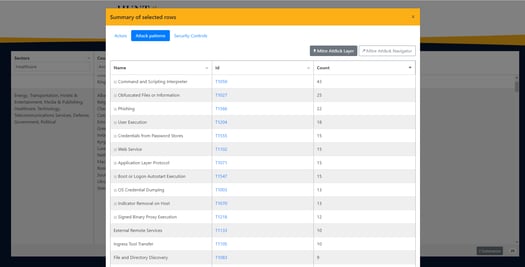 The rationale to pivot in this way, mapping TTP’s to security controls, is that it’s difficult to protect yourself against individual actors, as they continuously evolve. But you can protect yourself against their specific attack methods. This approach makes it much more difficult for threat actors to achieve their goal, as they will need to deviate from their preferred attack patterns and tools. This requires investments in time and resources. Some might decide to move on to the next target instead, whilst the ones that continue have a greater chance of being detected with Managed Detection and Response (MDR) and threat hunting, as they will have to work with TTPs that aren’t their preferred method for attacks.
The rationale to pivot in this way, mapping TTP’s to security controls, is that it’s difficult to protect yourself against individual actors, as they continuously evolve. But you can protect yourself against their specific attack methods. This approach makes it much more difficult for threat actors to achieve their goal, as they will need to deviate from their preferred attack patterns and tools. This requires investments in time and resources. Some might decide to move on to the next target instead, whilst the ones that continue have a greater chance of being detected with Managed Detection and Response (MDR) and threat hunting, as they will have to work with TTPs that aren’t their preferred method for attacks.
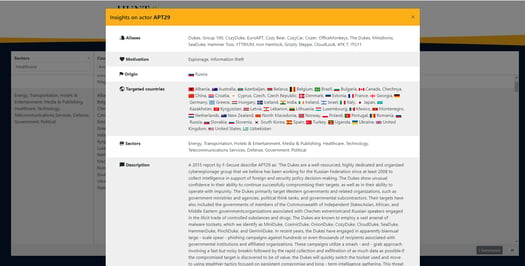 The threat diagnostics tool wires together existing threat intelligence enriched with our own threat actor data and knowledge. This results in a very complete dataset that provides a detailed picture of the threat landscape your organization faces, with data that is easy to navigate and presented in actionable summaries. Designed to provide organizations with a complete, meaningful overview of the threat landscape they are facing, the tool reveals where action is needed. Or, in other words, the tool helps organizations answering Sun Tzu’s key questions: “Do you know your enemy? Do you know yourself?”
The threat diagnostics tool wires together existing threat intelligence enriched with our own threat actor data and knowledge. This results in a very complete dataset that provides a detailed picture of the threat landscape your organization faces, with data that is easy to navigate and presented in actionable summaries. Designed to provide organizations with a complete, meaningful overview of the threat landscape they are facing, the tool reveals where action is needed. Or, in other words, the tool helps organizations answering Sun Tzu’s key questions: “Do you know your enemy? Do you know yourself?”
Data-driven versus fear-driven
Defending against threat actors has been the domain of fear, uncertainty and doubt for decades. However, our diagnostic tool helps CISOs to become data-driven instead of fear-driven. It will help you, and your team, to define and communicate a security policy that is goal-driven and transparent, with data at the core, that will outsmart your digital adversaries.
Contact us if you are interested to learn more about your digital adversaries. We’re happy to engage with you and share our view of the threat landscape for your specific organization.
Sources:
[1] https://attack.mitre.org/
[2] https://www.cisecurity.org/controls/
[3] https://nvd.nist.gov/800-53
[4] https://www.iso27001security.com/html/27002.html