- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Applied Threat Diagnostics
‘Knowing thyself’ in the world of Managed Detection & Response (MDR) requires an understanding of your threat coverage
As a CISO of an organization, that is active in an industry of interest to Advanced Persistent Threat (APT) actors, you have worked hard on building a security strategy, securing reasonable budgets, and the implementation of a range of security controls. Most likely you will have allocated a significant portion of your budget towards the detection of malicious activities in your networks, either by performing the necessary security operations internally, from your own SOC, or externally through an MSSP or MDR provider. In both cases, you are likely to have learned from experience that detection is not the fail-safe control that regulatory and compliance frameworks sometimes seem to suggest.
The key question to ask yourself is simple: “Do we have the necessary threat coverage in place to detect digital adversaries?” The answer however, isn’t that straightforward, as this question alone boils down to four sub questions. Each of these questions require data-driven, not fear-driven, answers:
- Who is targeting my organization and how do they operate?
- Am I monitoring the relevant data sources?
- Do I have the right detection technology in place?
- Do I have the right detection logic running to spot those threat actors?
To help our customers answer these questions, as part of their strategy to build a strong detection and response strategy, we designed unique Managed Detection and Response (MDR)/ Extended Detection and Response (XDR) services as fundamental part of the digital immune systems of our customers. XDR gives visibility into data across networks, clouds, endpoints, and applications while applying analytics and automation to detect, analyze, hunt, and remediate the past and future threats. Note that the focus for this blog will be primarily the technical side of XDR, the people and process side is pretty much out of scope for now.
(Managed) Detection and Response
Your immune system has many different elements, and so does the domain of Managed Detection & Response (MDR/XDR). Let’s take a deep dive into the three main elements that, together with detection, hunting and response processes, create that coherent system required to detect and stop malicious activity.
At Hunt & Hackett we believe that there are three core components/activities that should be part of your immune system, which in the end should be a never ending iterative process:
- Detection data sources: these are the data sources you need to monitor in order to detect malicious behavior;
- Detection technology: the required technology you need to ingest the data sources and apply the relevant detection logic;
- Detection logic: the indicators of compromise (IOC’s), detection rules and machine learning models that are used by the detection technology to detect malicious behavior within the ingested data sources.
How these three components will be embedded in your organization depends on your own threat model and threat landscape. That’s why threat modelling [1] is so important. A thorough understanding of the APTs you are facing, and the tools, techniques and tactics (TTPs) they use, makes it possible to determine which data sources are the most important to monitor. The MITRE ATT&CK framework helps in linking this together.
If you know the relevant detection data sources that need to be monitored by your organization, you can determine the type of detection technology that is capable of ingesting these. To name a few of the technologies for detection and response:
- SIEM (Security Information and Event Management)
- NDR (Network Detection & Response)
- EDR (Endpoint Detection & Response)
- Honeypots
The more data sources and the higher the quality [2] of the data sources covered by the detection technology, the more visibility you will gain, and the more APTs you will detect in your assets. After all, every detection tool monitors a different scope of attacks and ingests different data sources. Heatmapping the coverage of every piece of technology will give you directions on which detection technologies should have priority in your environment, and which detection technologies will help you to close the coverage gap.
With clear visibility in the data sources you need to monitor, and the detection technologies required to do so, it’s now important to understand the required detection logic to catch the bad guys. Mapping your threat landscape to detection logic will help you understand the techniques you need to be able to detect. This will also help you to determine which techniques you DO and DON’T cover from a detection perspective and where there is room to improve your detection logic.
Augmenting your detection logic can be done by either developing it yourself, use of public sources, or buying it (typically in the form of a managed service). Please note that knowing which techniques you do cover from a detection perspective is important, but knowing what you don’t cover is equally important. Not covering the detection of all techniques is fine, as long as you know it and as long as you are aware of the potential impact.
So in order to sum it all op, the picture below contains an overview how if all fits together.
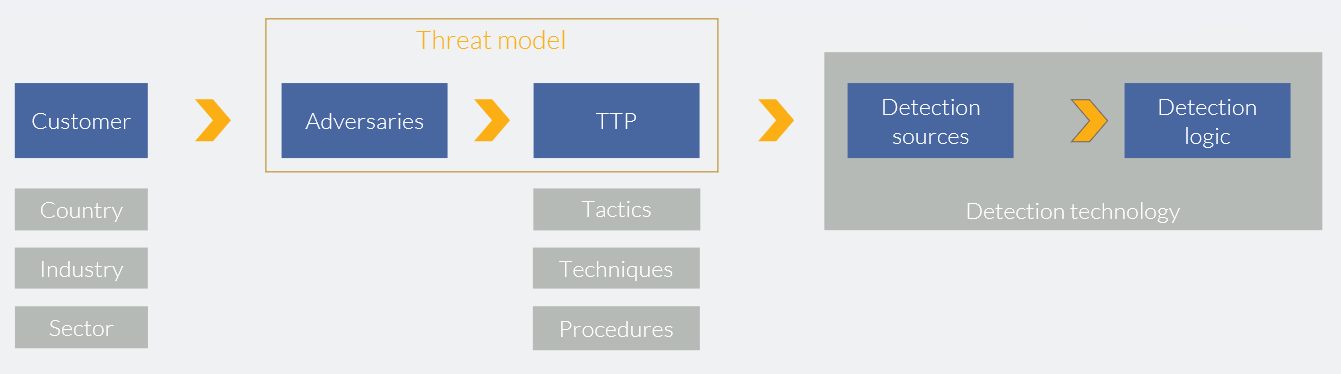 |
| Picture 1 – Translating the threat model into relevant detection sources, technology and logic |
Case study
Let’s assume you are an industrial company operating in The Netherlands. If we, at Hunt & Hackett, apply our threat diagnostics tool to your sector and geographical area, this would result in an overview of 15 relevant threat actors for your organization and the corresponding attack techniques. See picture 2 for a snippet.
If you subsequently map out the data sources to detect the techniques of threat actors yielded by the threat diagnostic tool, you would get an overview of 52 data sources as shown in the snippet (see also picture 3). Sorting the occurrence of the data sources in a descending order, would tell you which data sources should get the highest priority and cover the most techniques deployed by your relevant threat actors.
Picture 4 presents an overview based on a priority score (the higher, the more important) of the applicable technology that gives you the best and most coverage and visibility, taking into account the techniques used by the threat actors that are relevant to you. For your specific threat landscape, the tool suggests that log monitoring (44,5%) offers you the most bang for the buck from a coverage and visibility perspective. As a close second end point monitoring (42.9%) and lastly network monitoring (12,6%). This insight will help you to make the right technology choices within your budget and determine future priorities.
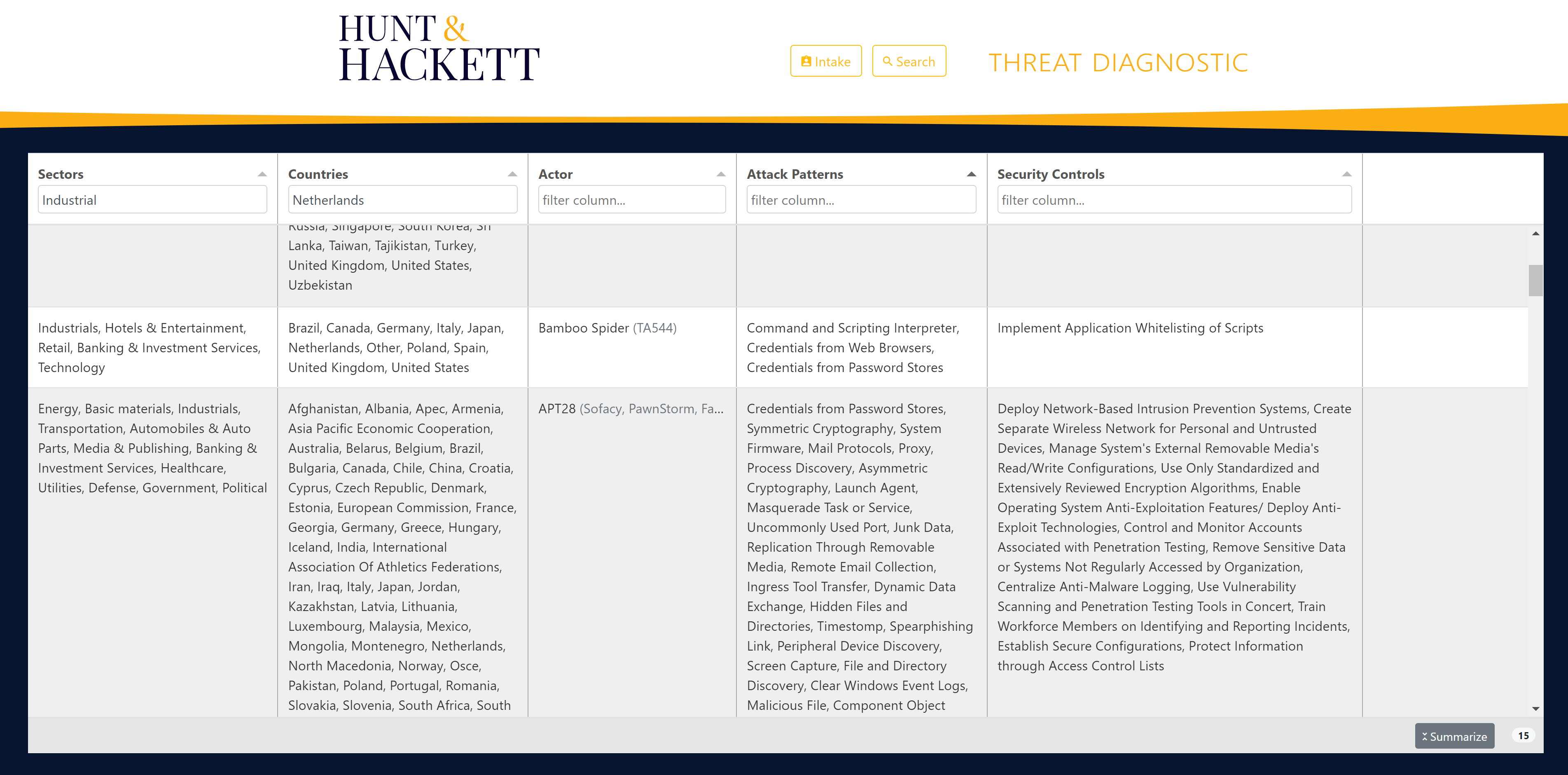 |
|
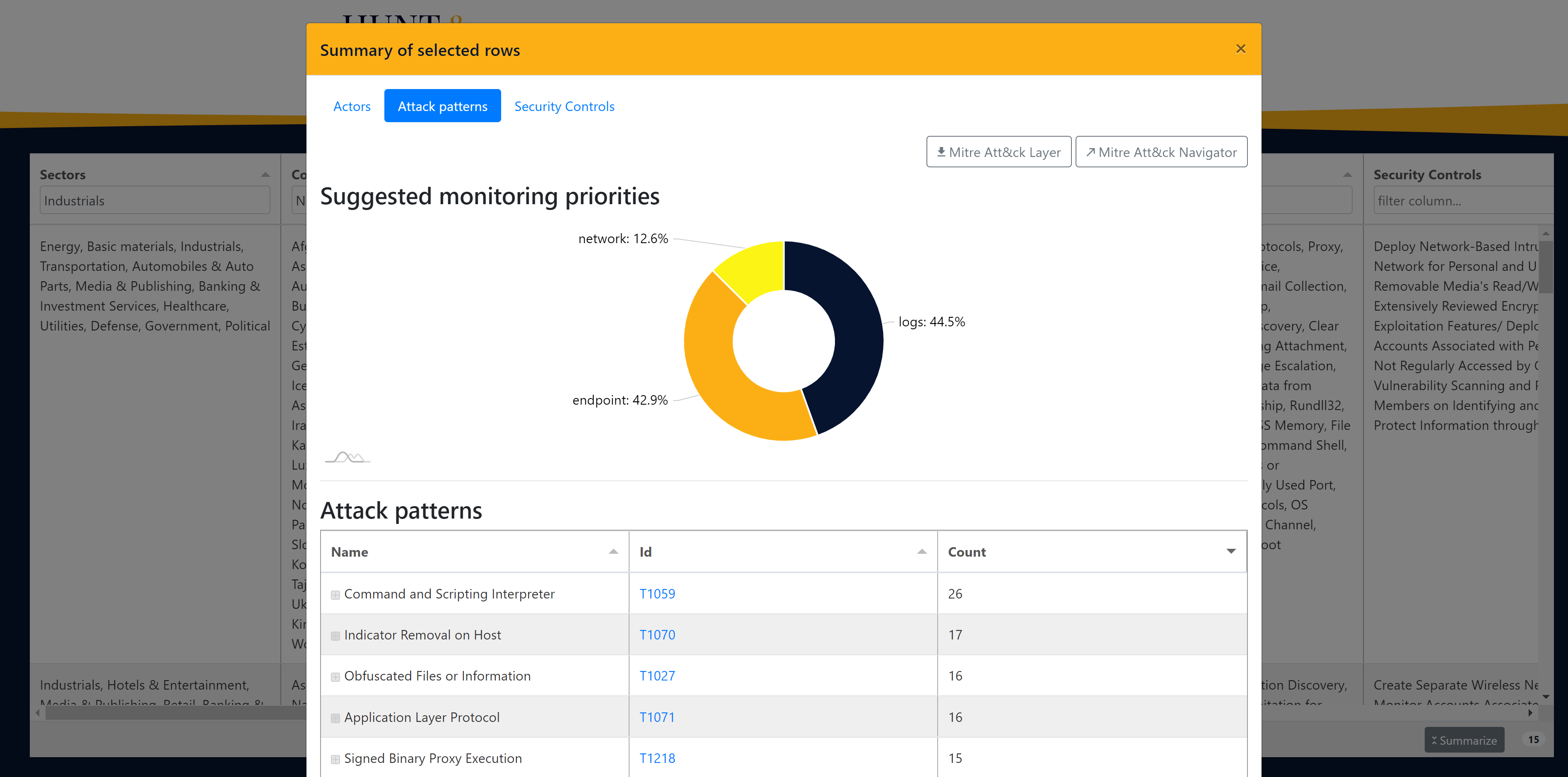 |
| Picture 2 - Threat landscape | Picture 3 - Overview of attack patterns | Picture 4 - Technology priority |
Please note that our threat diagnostics tool is under continuous development, which will over time result in more granular mitigations and mapping to detection logic. Hunt & Hackett can provide you with an overview of your threat landscape, the relevant data sources and required technology. By assessing the detection technology you are using and the data sources ingested at this moment in time, you get an understanding of your current situation. The outcome of this assessment can be mapped to the Hunt & Hackett threat model output, in order to determine the discrepancy and decide on whether that is acceptable.
Our threat modelling approach is acting upon ancient Chinese general Sun Tzu's key insight: "Know thy enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle." This approach is adversary-driven and at the heart of how we at Hunt & Hackett enable CISOs around Europe to outsmart their digital adversaries.
Let us help you answer the question
In this blog we focus on the important question whether or not your organization has the necessary threat coverage in place to detect your digital adversaries. Answering this question is possible by identifying your threat landscape (threat modelling) and then translating this into a strategy to enable your organization to monitor the relevant data sources for detection, to implement the right detection technologies and logic.
At Hunt & Hackett we use this data-driven approach to provide our customers with measurable, objective and transparent advice on how detect and respond to relevant threats. Furthermore, we deploy a modern MDR stack that will be tailored to the specific threat landscape of our customers. Combined with the required insight into where our customers are protected and where the gaps are that need to be closed, we create the necessary evolving digital immune system our customers need.
Sources:
[1] https://www.huntandhackett.com/blog/threat-modelling-as-starting-point[2] https://github.com/rabobank-cdc/DeTTECT/wiki/Data-quality-scoring#Data-quality-dimensions