- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
The SolarWinds attack: A contrarian view and lessons learned
December 2020. Press agency Reuters reported a large hack at SolarWinds, a software company not many people had heard of at the time. Quickly it became known that SolarWinds was used widespread, particularly by IT-companies to maintain infrastructure for their clients. So, while SolarWinds was relatively unknown, the attack turned out to have far reaching consequences for many organizations all over the world, including US government agencies such as the Treasury Department and Homeland Security. For months, hackers had access to SolarWinds’ Orion IT monitoring and management software which required privileged access to the systems it manages. Through that access, the attackers could roam freely through sensitive and usually heavily protected data within systems of high-profile targets. Truly novel, yet unknown, and even some undetectable methods were used to infiltrate the IT-giant’s software. Undetectable means nothing can be done to detect these attackers while they are actively trying to gain a foothold within your network, right? Well, not so fast.
To understand how undetectable the SolarWinds attacks was(n’t), it is vital to understand how a sophisticated cyber-attack works, how attackers move through systems and how even the most sophisticated attack can be detected if Detection and Response measures have been set up right. With this publication Hunt & Hackett does not claim that it would have detected the SolarWinds attack with our MDR-service while the attack was ongoing. We analyze such attacks with the aim to improve our understanding, and to see whether lessons can be learned from it to improve our detection capabilities. When we feel it provides meaningful new insights than we like to share our these insights with the wider security community such as with this blog.
The attack
In December 2020, cybersecurity company FireEye was investigating a breach of their own infrastructure, when the security team tasked with the investigation discovered something peculiar: the hack was not limited to their own network, but originated from their supply chain. The researchers figured out that the initial foothold could be traced back to software company SolarWinds’ product ‘Orion’. Through an update, the Orion IT management software installed a backdoor into the networks that it was used in. FireEye, who made the discovery, named the malware ‘SUNBURST’. Once the infected update was completed, hackers obtained access to the targeted organizations’ cloud-based services through the authentication granted via the Orion software. This attack phase was dubbed TEARDROP. This phase was aimed at exploiting the backdoor in the network of the organizations on the attacker’s wish list out of all organizations infected. In the weeks that followed the discovery, the unprecedented scale of the attack began to unfold. Numerous leading companies and organizations got blindsided by the exploited weakness in their trusted vendor’s software. Among these organizations were the very ones from who you can expect to have their security meet the highest standards, such as tech companies Microsoft, Intel and Cisco. Quickly it became known that over 18,000 SolarWinds clients had performed the SUNBURST update. Other known and notable victims were the U.S departments of Homeland Security, Commerce and Treasury. Even the National Nuclear Security Administration, responsible for maintaining the U.S. nuclear stockpile, did not manage to fend off the attack. [1]
According to the U.S. intelligence community, evidence pointed at a very large group of hackers acting on orders of the Russian government with the purpose of gathering intelligence on a variety of subjects. Later, Microsoft identified the APT ‘Nobelium’ to be responsible for the attack.
"Researchers believed at least 1,000 very skilled, very capable engineers worked on the SolarWinds hack. This is the largest and most sophisticated sort of operation that we have seen.”
-Brad Smith, Microsoft President in Congressional Hearing, 23rd February 2021. [2]
The researchers investigating the SolarWinds hack discovered that initial access had been established by the attackers in September 2019. It took a total of 14 months before FireEye noticed the breach and initiated an investigation. Threat detection measures were cleverly circumvented, mainly because of the level of sophistication of the attack. Nobelium used some attacking methods that were never seen before and forensic tools at that moment could not detect. This is where the paradox comes in: it is quite often possible to detect an attack that uses undetectable initial footholds.
Detecting the undetectable
A commonly used and justly appraised approach in cyber-security is Threat Modelling. In this approach, the focus lies on mapping the threat landscape to see what APTs’ preferences are, so a defense can be set up against them. This approach is centered around observed attacks and the methods used in it. However, threat actors of the highest sophistication use new attack methods that are unknown and are thus far for the most part undetectable. For an explanation of the threat detection lifecycle, see figure 1 below. Setting up defenses is quite hard in that situation. How would one raise walls against an enemy that might be able to fly?
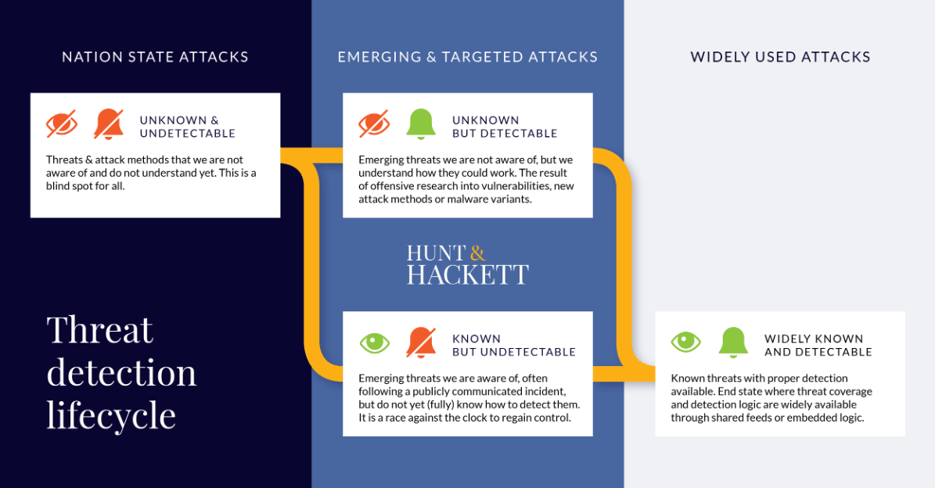
Figure 1 – The stages of the threat detection lifecycle.
The SolarWinds initial attack fell in the category of unknown & undetectable. Methods that fall into this category are extremely difficult to detect and fend off. However, as is the main argument of this article, even the newest and most sophisticated attacks often contain elements that are Unknown & Detectable, Known & Undetectable or even Known & Detectable, and can therefore be noticed with the right set of tools. A sophisticated cyber-attack generally consists of several phases, depending on the goal of the attack and the attackers’ modus operandi. During the SolarWinds hack, in only two out of eight phases Unknown & Undetectable methods were used: Initial Access and Defense Evasion. To detect an incident in these phases is extremely hard and requires a great deal of luck. However, when one looks at the entire attack chain a more positive picture emerges. In all eight phases, nine TTPs were used, of which only two were Unknown & Undetectable, and one Known & Undetectable. This leaves six TTPs that could have been detected based on existing knowledge and techniques at the time: TEARDROP CobaltStrike beacon, use of victim hostnames for C2, lateral movements using valid accounts other than initial access, temporary file replacement, temporary task modification and resulting hands-on keyboard attack. Also, it is possible to detect TTPs that fall into the Unknown & Detectable category. This is not easy and time consuming, because it requires specific behavioral monitoring instead of the low-level Indicators of Compromise (IOCs) that are based on known attacks, as is common practice for a large part of the MSSP- and MDR- providers. Behavioral monitoring goes beyond just looking for IOCs, and maps its clients’ specific networks, which is a custom process that, despite of the promise of machine learning and AI, typically requires significant time and expertise to embed in security operations. Most cybersecurity providers do not apply this less efficient method because for every client it needs to be tailored. When used correctly, however, it drastically ups the quality of detection and make it possible that ensures that even the most advanced attacks will may not go unnoticed.
APTs expose themselves when moving around in networks, using TTPs that are known and can be detected. Carefully monitoring lateral movement by the attackers for example, could have resulted in earlier detection. Highly sophisticated actors have the ability to develop or acquire some Unknown & Undetectables, but are very unlikely to use them extensively, just for the fact that it is extremely hard and time consuming to develop them. APTs are going to have to resort to detectable or at least known techniques if they want to succeed and be efficient in their attacks. So how does this translate into the SolarWinds attack? As figure 2 shows, there were eight phases to the hack. The TTPs applied by the intruders only had Unknown & Undetectable elements (1 and 4) in Initial Access and in Defense Evasion. Several phases following the Initial Access and Defense Evasion consisted of Unknown & Detectable elements (2, 3, 5, 6 and 7), which are difficult to detect but doable with the right security measures implemented, as has been described above. If SolarWinds or their (ultimate) clients had been prepared for cyber-attacks of the highest level of sophistication and had set- up appropriate detection measures (and thereby relied more on behavioral detection), the attack could have been discovered while it was ongoing much earlier, mitigating its disastrous effects.
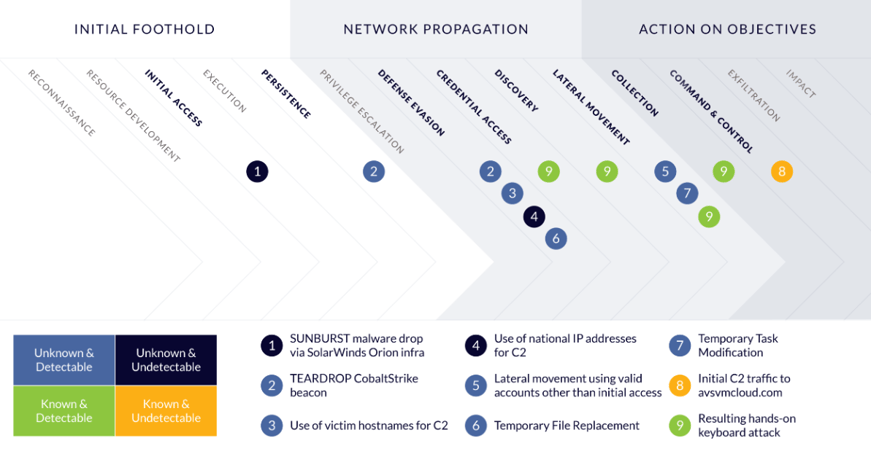
Figure 2 – The phases of the SolarWinds attack and the TTPs used.
The Hunt & Hackett way
Hunt & Hackett protects its client’s most valuable assets, such as their Intellectual Property (IP), sensitive data and other company secrets by providing tailored detection logic to specific customer situations. In addition, to improve the resilience of its partner organizations, Hunt & Hackett applies properly aligned security monitoring, prevention, and incident readiness measures. Together these pieces form the puzzle that safeguards organizations in a worrisome threat landscape against both untargeted as targeted sophisticated attacks, even most Unknown & Undetectable threats can eventually be addressed. This puzzle is not easy to solve. However, Hunt & Hackett applies a variety of (custom) methods and techniques to address its customers specific security-needs. In a recent article [3], the Hunt & Hackett proposition is thoroughly explained.
Contact us at info@huntandhackett.com if you want to know more about identifying and eliminating blind spots in detection and what we can do to help you control your cyber-security risks.
Sources
[1] https://www.csoonline.com/article/3613571/the-solarwinds-hack-timeline-who-knew-what-and-when.html
[3] https://www.huntandhackett.com/detecting-targeted-attacks
TAGS: #Solarwinds, #SUNBURST, # TEARDROP, #Nobelium, #Undetectable, #Hindsight