- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Manufacturing industry under attack due to cyber threats
Manufacturers all over the world are prone to a multitude of cyber-attacks that was unheard of a few years before. Hacker-groups, also known as APTs, have suddenly generated interest in this particular industry. In this blogpost, Hunt & Hackett explains why this sudden surge has occurred, what motives lie behind the attacks, and who the agressors are. Moreover, it is examined what can been done to protect your business.
Introduction
Over the past years, manufacturing has climbed the ladder of most-attacked industries by a worrying pace. Every few months, news pops up about a new cyber-attack on a major manufacturer. Some of these attacks make headlines, because of the widespread consequences attacks on manufacturers can have on other parties involved. This is what Dutch firm VDL discovered after it was infected with ransomware, but the ramifications of the halting of its operations spread to other companies in its supply chain. However, the cases that are hitting the news are just the tip of the iceberg. In reality, there are many more cyber-attacks, daily happening to thousands of companies worldwide. So, what is so special about the manufacturing industries and why does it seem that only recently the industry has really come into the crosshairs of cyber-attackers? As shown in Figure 1, the IBM Security X-force data shows that in 2019 the manufacturing ranked 8th out of the most attacked industries. Just one year later the sector ranked 2nd. To fully understand this growing threat to the industry, Hunt & Hackett has dived into the world of manufacturing and its lurking adversaries. At the base of Hunt & Hackett’s thought leadership lies the idea that one must know themselves and their adversaries to stay multiple steps ahead, or as the famous general Sun Tzu wrote: “if you know the enemy and know yourself, you need not fear the outcome of a hundred battles.” That is why Hunt & Hackett does not just study the hunter, but also the hunted.
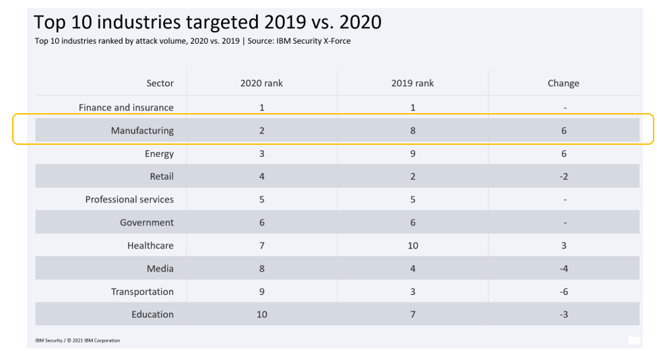
Figure 1 - The manufacturing industry has caught the eye of hacker groups | Source: IBM
.
The outlook of manufacturing
Manufacturing is a broad business ranging from food processing to the assembly of rockets. Companies that make up this industry differ greatly in what they manufacture but despite this variety, they have become a target of criminals and nation-states altogether. According to World Bank data, manufacturing makes up 16,5% of value added to the world’s GDP. This comes down to a staggering amount of yearly $14.5 trillion that is generated through manufacturing, a figure that has nearly tripled over the last 25 years. The biggest players in the game are China, the US, Japan, Germany and India. Together they account for over 60% of added value by manufacturing to the global GDP. China, also nicknamed ‘the world’s factory’, is by far the largest manufacturing country, which accounts for around 27% of its GDP, significantly higher than the world’s average of 16%. Manufacturing products for the rest of the world has given China the opportunity to grow into the position of power they are in today.[2]
Trends and challenges
Like any other industry, the world of manufacturing is constantly evolving. The world is changing faster and faster, and manufacturers have to keep up pace to maintain their competitiveness. With much of the manufacturing having been offshored over the last decades, the manufacturing that is done in western countries has increasingly been high-tech manufacturing, utilizing innovations in manufacturing technologies. Current trends that are occurring in (western) manufacturing are part of the reason why in recent years the industry has seen a striking increase in cyber-attacks. The main trends and challenges in manufacturing are industry 4.0, a lack of skilled workers, cyber-security, and rising cost of transport, of which the first and third trends are the most relevant for malicious hackers. Why the other trends are also briefly explained, is because to fully understand the threat to the industry, it is vital to understand what manufacturing as a sector looks like.
Industry 4.0
The trend to watch in the manufacturing industry at the moment is industry 4.0. The fourth wave of industrialization is rocking the world of manufacturing. Technologies that are reshaping the outlook and practices of the industry are being adopted at an increasing pace. The most important of these technologies are connectivity, analytics and intelligence, human-machine interaction and advanced engineering, as is depicted in Figure 2. The new possibilities allow manufacturers to do so much more, from producing more efficiently to monitoring processes more carefully. Industry 4.0 makes rapid prototyping possible. We see technology driven companies like Tesla, SpaceX, ASML and niche players like Koenigsegg, becoming highly vertically integrated. They are bringing as much of the manufacturing in-house as possible to control all aspects of the product. This has created an innovation cycle at a both a depth and speed that was previously unheard of. Industry 4.0 is therefore transforming the manufacturing industry drastically as it is making onshoring manufacturing more viable in economic terms. This trend was already occurring, but caught a tailwind as a result of covid-19, the global supply chain challenges, rising transportation costs and escalating global political tensions.[3]
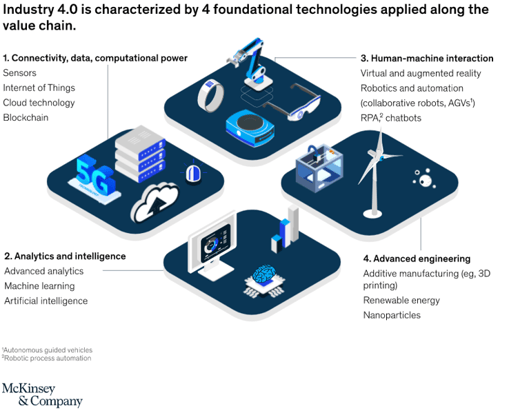
Figure 2 – The foundational technology of industry 4.0 | Source: McKinsey & Company
.
Lack of skilled workers
Despite all the benefits that industry 4.0 brings along, there is also same bad news for manufacturers that comes with it. First is the lack of skilled workers. The changed nature of work in manufacturing is to blame for the shortage of properly schooled employees. In the past, manufacturing consisted of highly intensive physical labor, dating back to the first industrial revolution. Nowadays, the world is going through the transformation of the fourth industrial revolution. Additionally, the exodus of the enormous boomer-generation has started, and they don’t leave their skills behind. The starting adequately schooled workers aren’t joining the labor market in large enough numbers, and so a gap is created. For the U.S. alone, there is an expected shortage of over two million workers over the coming years.[4]
Rising costs of transport
In recent years, the cost of transporting goods from one place to the other has soared. The demand for shipping is way too high to satisfy for companies active in logistics and shipping. Prices for shipping containers have been surging for the last few years and likely will be for the time to come. In 2019, a container on a ship from Asia to the U.S. cost around $1.500 dollars. Expectation is that this will reach at least $6.500 in 2022. Shipping capacity is being expanded but will only be ready in 2023 at the earliest. This won’t fix the problem, as structural investments are needed in all links of the supply-chain, such as ports and roads. It will take years before the problem is resolved. Until then it is unlikely that prices drop. Manufacturers will need to find a way to keep their products profitable and timely delivered. More recently the energy prices have soared, due to the Ukraine war. This will have an impact on energy prices for at least the medium-term and possibly long-term, that will further affect not only the cost of transportation but likely the cost of manufacturing as a whole.[5][6]
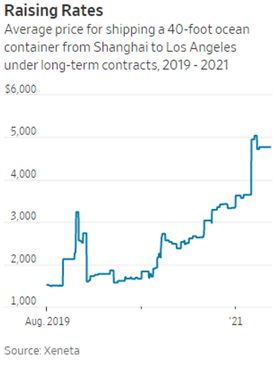
Figure 3 – Prices for shipping containers have skyrocketed since 2019 | Source: Xeneta
Cyber-security
For manufacturers, the advent of industry 4.0 is a pot of gold, but security wise can also turn into pandora’s box. The new technologies provide manufacturers with faster and more efficient producing processes, but at the same time opening the door for malicious cyber-attackers. Manufacturers are massively connecting their Operational Technology (OT), like Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems and Internet of Things (IoT) devices, with each other through internal networks of directly through the internet. These systems often run on outdated or self-developed software that is often just target practice for hackers to crack open. When poorly secured ICS and SCADA are taken over by hackers, they have three choices: (1) paralyze the ICS with ransomware, (2) build up persistence throughout the network the ICS are connected with and infect other networks to have a foot between the door whenever need be, or (3) to spy on the practices and steal IP from the targeted organization.
Then, there is the problem of the ‘transparent supply chain’. Suppliers, companies and customers build trust between each other by opening up their part of the supply chain. It has many benefits, but there is a problem for cyber-security as well. The already wide attack surface in manufacturing becomes even wider, as organizations in the supply chain connect their IT and OT systems to each other, while their cyber-security measures are often inadequate and fragmented. As a consequence, organizations are as strong as the weakest link in the supply chain. This became painfully clear when in 2013 American retailer Target fell victim to a cyber-attack. Through one of their vendors, a refrigeration manufacturing company, hackers forced their way into Target’s networks. The networks of both companies were connected for the purpose of electronic billing amongst others. The hackers infiltrated Target and stole credit, debit and customer records from around 70 million clients. Target was fined $18,5 million, but the cost of the breach is estimated to be over $200 million.[7]
The threat
Manufacturers face a multifaceted cyber-threat. From ransomware to IP theft, there is a variety of reasons for malicious actors to set their sights on organizations active in manufacturing.
- Manufacturing is highly susceptible to ransomware-attacks because it is capital intensive and has a great dependency on continued operations. The impact of downtime is far more severe than let’s say that of a law firm.
- IP theft is useful for several purposes, for rivaling companies or even nation-states. Innovation and Intellectual Property (IP) is what one manufacturing company differs from the other. IP theft is often overlooked, yet it is the main motivation for cyberattacks on the sector. IP theft, and espionage in particular, is often carried out by highly sophisticated threat actors. These attacks are much less often disclosed by targeted organization due to the potential (long-term) ramifications when they fell victim to such attacks. The consequences are not merely reputational but can also directly affect the stock price as the attacks are aimed to impact the long-term cash-generating ability of the organization. Some espionage cases within the sector are widely known, such as when ASML - a global leading semiconductor equipment manufacturer - was robbed of important IP by Chinese nationals in 2015.[8]
- Manufacturers can also be used as gateways to other organizations in the supply-chain, in so-called supply-chain attacks. This was the case in the earlier mentioned Target hack.
Nation-states carry out cyber-attacks for several reasons. They can be looking to sabotage their adversaries, have financial motivations, or, as is increasingly the case, are looking for ways to use cyber-attacks as a means of financial and economic advantage. The use of cyber-espionage to uncover foreign company secrets for the benefit of their own economy is becoming mainstream among many countries. Nation-states from all over the world already have policies in place that allow them to use their intelligence apparatus for economic gain. Friend or foe, no one is safe from their highly sophisticated offensive cyber-operations.
In manufacturing this is no different. Hunt & Hackett has observed four nations to be the most active in the pursuit of cyber-espionage in this particular industry: China, Russia, Iran and North Korea are the top aggressors, see the table below. In the recent Hunt & Hackett series of blogs on the maritime industry, it is extensively explained what motivates each of these four countries to be this aggressive with their cyber-force.
| China | Russia | Iran | North Korea | |
| Key strategic objective(s) | Modernizing their ‘factory of the world’ in line with the ‘China 2025’ policies | Make modernization possible despite international sanctions | Make modernization possible despite international sanctions | To improve the financial and economic situation in a hostile international environment |
| Level of cyber capabilities | Medium/High | High | Medium | High |
| Known motives for cyber deployment | Espionage; Information Theft | Financial Crime; Financial Gain; Espionage; Information Theft | Espionage; Information Theft | Espionage; Information Theft; Financial Crime |
| #APT groups | 50 | 39 | 19 | 7 |
| #TTPs | 689 | 700 | 351 | 152 |
| #Tools | 195 | 458 | 227 | 208 |
Table 1 – Key stats on the most actively attacking nations in manufacturing: China, Russia, Iran and North Korea.[9]
In table 1, the key strategic objectives and statistics of the most aggressive nations in manufacturing worldwide are displayed. As can be seen, China employs the most hacker groups, or Advanced Persistent Threats (APT). The different kinds of behavior of these threat-actors are described using the TTPs (Techniques, Tactics and Protocols). Tools are the software these APTs use to gain access to targeted systems and build up persistence or infect them with malware. By tracking used APTs and their preferred TTPs and Tools, Hunt & Hackett safeguards its partners from them.
The role of the Netherlands
The Netherlands is home to some of the largest manufacturers in the world. Some of these international giants were founded in the Netherlands, such as Unilever and Heineken, both manufacturers of food and beverages. Other renowned Dutch-founded companies include Philips, AkzoNobel, DSM, ASML, and Damen. There are also companies that have large production facilities in the Netherlands due to its strategic positions as gateway to Europe, which is exploited the most through the Port of Rotterdam, the largest seaport of the continent. Dutch manufacturers are well-known for the quality and reliability of its products, as well as the high rates of automation and innovation.[10]
| Company Name | Revenue (x billion) | Specific Industry |
| Unilever | €66,7 | Food & Beverages, Personal Health |
| LyondellBasell | €46,6 | Chemicals |
| Philips | €32,7 | Electronics |
| Heineken | €24,3 | Food & Beverages |
| AkzoNobel | €20,3 | Chemicals |
| DSM | €9,2 | Various |
Table 2 – Some of the largest manufacturers that are headquartered in the Netherlands.[11]
With a manufacturing industry of this size, it is no surprise that the Netherlands have caught the eye of foreign entities with bad intentions. In 2020, Dutch intelligence dismantled an illicit Russian network that had set its sights on the high-tech industry in the Netherlands.[12] As a result of this discovery, Dutch lawmakers are moving to penalize foreign espionage for economic purposes. Another incident, this time directly impacting the public, was the ransomware hack of Bakker, a large Dutch cheese-logistics company. The cheese shelves in supermarket remained empty for a few days, again indicating the fragility of the supply-chain. That manufactures in the Netherlands have caught the attention of hackers recently became very clear. Family business VDL Groep (€4,7 billion revenue in 2020), which is active in the manufacturing of among others cars and parts, got hacked in October 2021. Although little information on the attacks was disclosed by the victim, it is known that it concerned a ransomware attack, that is rumored to be attributed to a Russian APT. Due to the hack, all digitalized and automated processes of VDL had to be halted for weeks. Further down the supply-chain, mega manufacturers Philips and ASML got in trouble because of the VDL hack. The halting of operations at VDL was cause for delay in the operations of their business partners. Another clear example of the ripple-effect cyber-attacks can have in the supply-chain of manufacturers.[13]
Conclusion
The highly varied manufacturing industry is no longer safe from cyber-threats, but has become a prime target altogether. This can be blamed on many things, but a few reasons stand out. The advent of industry 4.0 has drastically widened the attack-surface due to the interconnectedness of systems and networks that were never designed to be connected in the first place, let alone to the internet, as is often the case. The poorly (if at all) secured Operational Technology can be easily breached by third parties with bad intents and the right skillset. The transition of manufacturing technology from ‘stupid’ to ‘smart’, or disconnected to interconnected, is a pitfall of terrific proportions in terms of cyber-security. Manufacturers should not just be aware of their own cyber-hygiene, but also that of their supply-chain, as this has become interconnected as well. Hackers are known to target vendors and other parties further along the supply-chain in order to find a way to their initial prey. Consequences of being hacked as a manufacturer can be far-stretching; from companies losing control of their operations for weeks to customer data being stolen with mega fines as result.
Manufacturers have a lot on their mind these days. Keeping up with disruptive technologies, volatile international politics, conflicts, a lack of skilled workers, rising costs of transport and cyber-security. Hunt & Hackett provides its partners with one less thing to worry about. So, what to do with this threat landscape information? The Hunt & Hackett sector specific blog-series have two goals: (1) to raise awareness and educate organizations about their threat landscape and (2) to give organizations insight into how Hunt & Hackett defends its partner against sophisticated and specific threats. Hunt & Hackett works with innovative companies, in manufacturing and related industries, that invest a great deal in their R&D departments and want to keep their (trade)secrets just that: secrets. The approach we provide our customers with is data-driven, and focuses on the adversary: what attacking techniques do they apply and how can we defend from them? This is the reason why Hunt & Hackett tracks APTs, their TTPs and Tools. In cyber-security, this adversary-central approach is also known as Threat Modelling.
Threat Modelling is required to make the threat landscape actionable. In this approach, the TTPs and Tools of a set of relevant adversaries form the basis to build-up the defenses of an organization. This specific threat picture can then be translated into specific security controls (e.g. CIS, NIST, ISO) and data-sources to log and actively monitor. How this can be done is outlined in some of our previous blogs:
- Threat Modelling as starting point;
- Applied Threat Diagnostics;
- Insights: the driving force behind a digital immune system.
Sources
- https://securityintelligence.com/posts/threat-actors-targeted-industries-2020-finance-manufacturing-energy/
- https://www.macrotrends.net/countries/WLD/world/manufacturing-output
- https://www.mckinsey.com/business-functions/operations/our-insights/industry-40-reimagining-manufacturing-operations-after-covid-19
- https://www.nam.org/2-1-million-manufacturing-jobs-could-go-unfilled-by-2030-13743/
- https://www.wsj.com/articles/shipping-and-logistics-costs-are-expected-to-keep-rising-in-2022-11639918804
- https://www.cnbc.com/2021/11/03/supply-chain-bottlenecks-will-take-time-to-resolve-shipping-firm-ceo.html#:~:text=Bottlenecks%20in%20global%20supply%20chains%20have%20threatened%20the%20supply%20of,higher%20for%20longer%20than%20expected.
- https://www.bankinfosecurity.com/target-vendor-acknowledges-breach-a-6489
- https://www.reuters.com/article/us-asml-china-spying-idUSKCN1RN0DK
- Hunt & Hackett Threat Diagnostic Tool
- https://www.tauron.nl/blogs/nederlandse-maakindustrie/
- https://manoxblog.com/2018/09/22/list-of-largest-european-manufacturing-companies-by-revenue-2/
- https://www.aivd.nl/actueel/nieuws/2020/12/10/aivd-rolt-spionagenetwerk-op-in-nederland-twee-russische-inlichtingenofficieren-moeten-het-land-verlaten
- https://www.1limburg.nl/vdl-aangevallen-door-russische-hackers