The new NIS2 Directive will significantly change what cybersecurity measures are required from public and private organisations falling under its scope. Once the scope assessment determined that NIS2 is applicable, the next step in an organisation’s preparation is to explore what CIS Controls are missing from their current security framework. However, due to the high discretion Member States are provided in the implementation and interpretation of NIS2, it remains to be seen what the exact measures will be. Member States have until 17 October 2024 to adopt their version of NIS2.
Furthermore, the Directive lays down strict incident reporting deadlines, requiring entities to report every significant incident in 24 hours with a follow-up and more detailed report in 72 hours. The final report needs to be submitted in one month, including “(i) a detailed description of the incident, including its severity and impact; (ii) the type of threat or root cause that is likely to have triggered the incident; (iii) applied and ongoing mitigation measures; (iv) where applicable, the cross-border impact of the incident.” This is an extremely short time period to produce such a document, which means that in order to comply with NIS2, companies need to have high level of maturity in their cybersecurity processes.
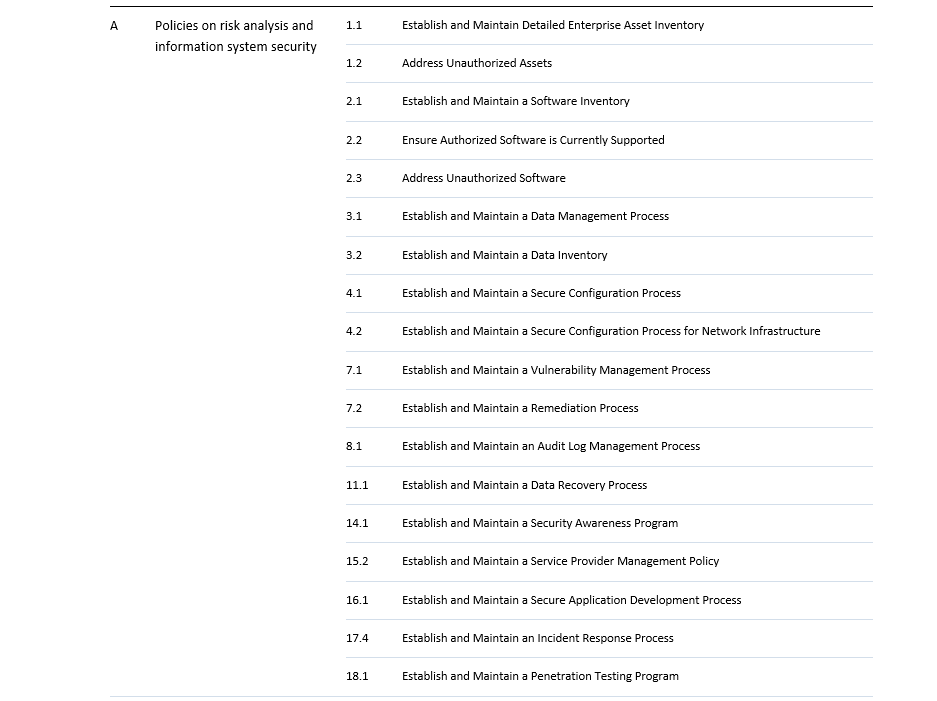
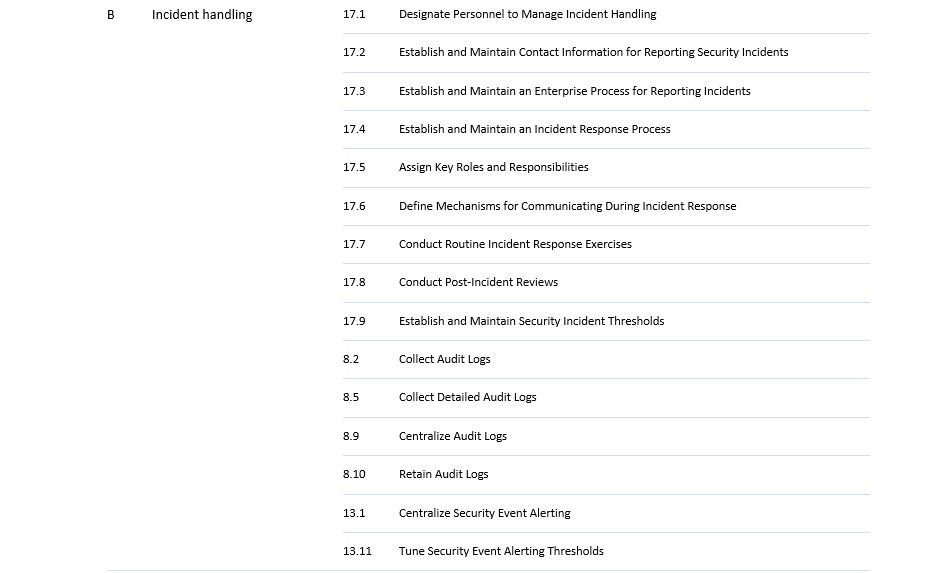
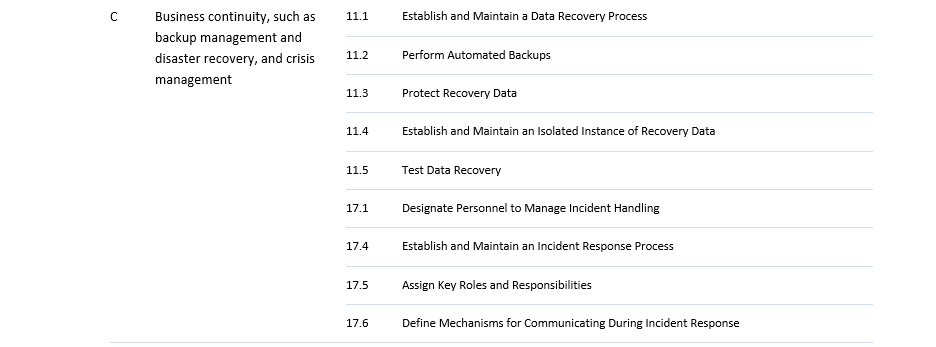
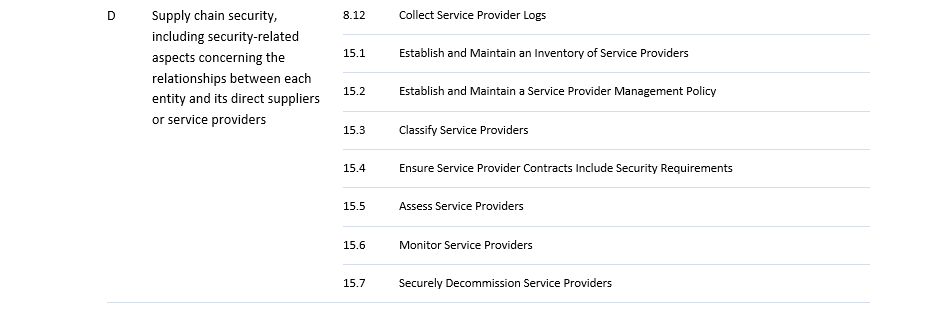
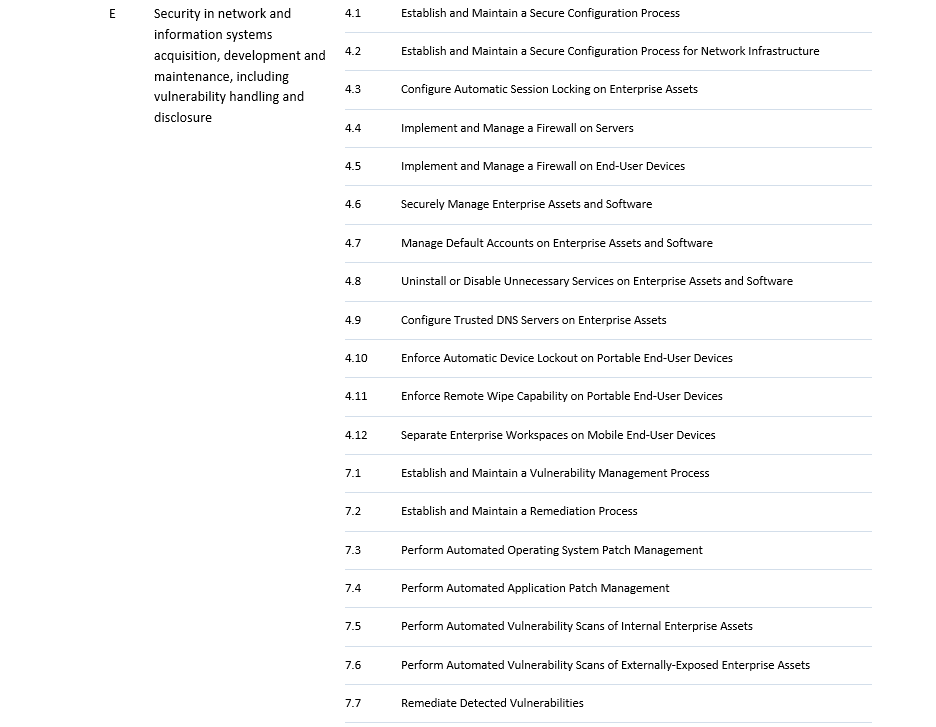
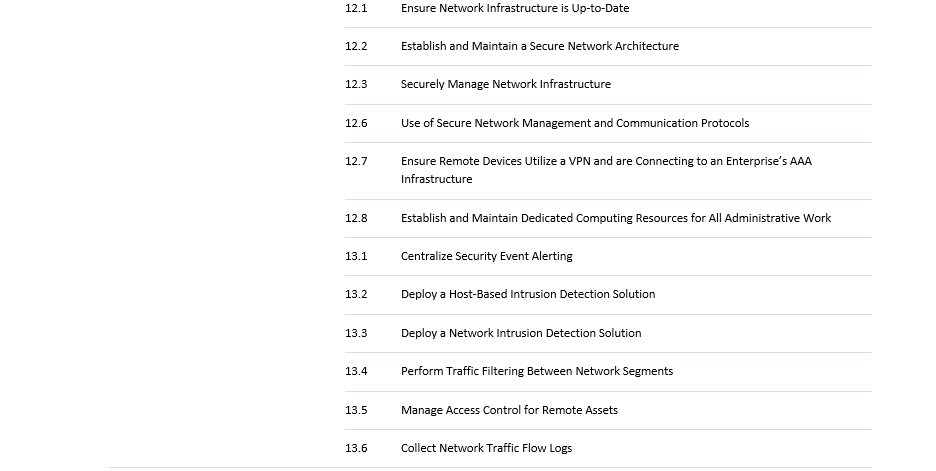
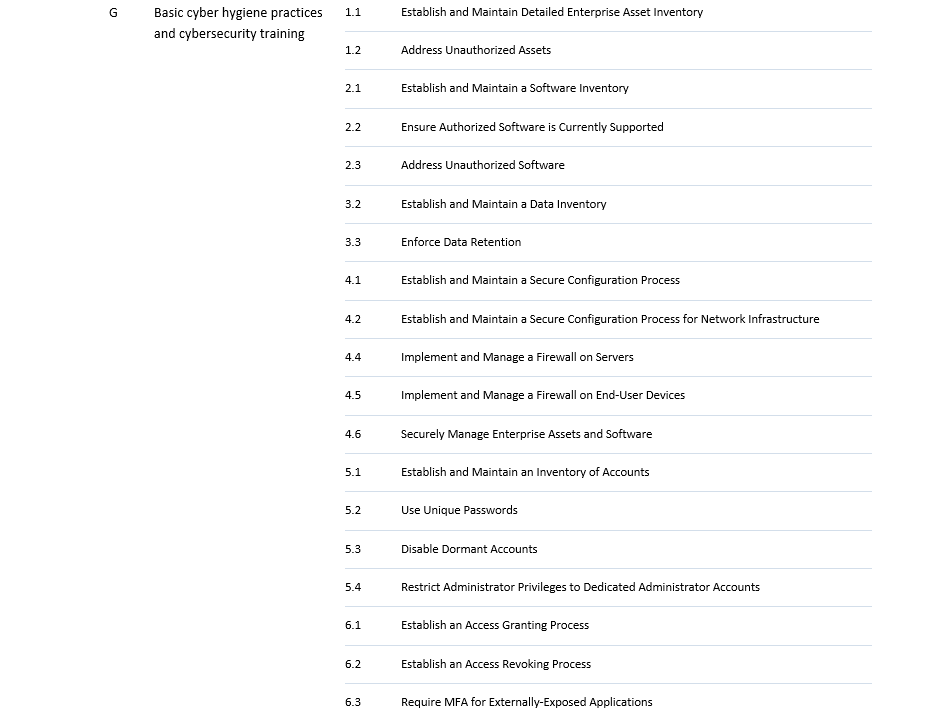
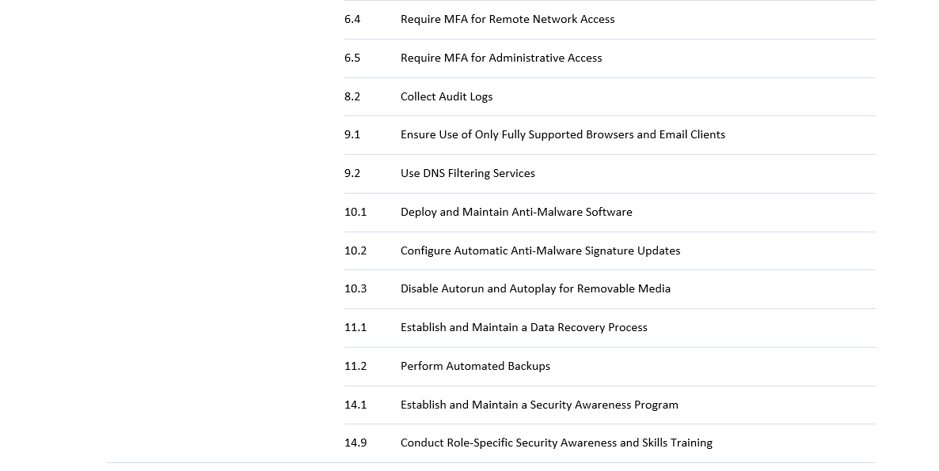
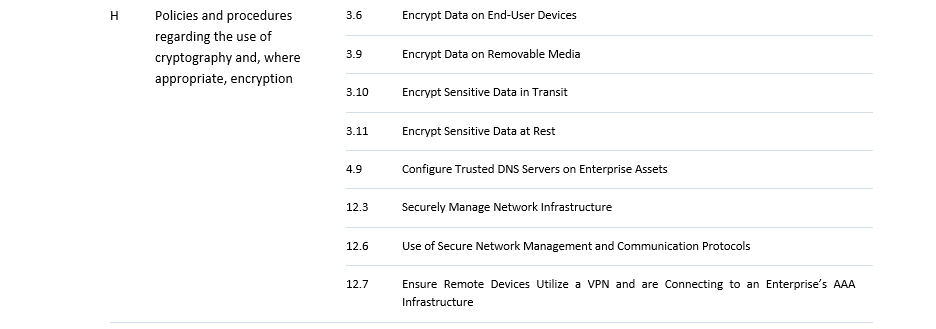
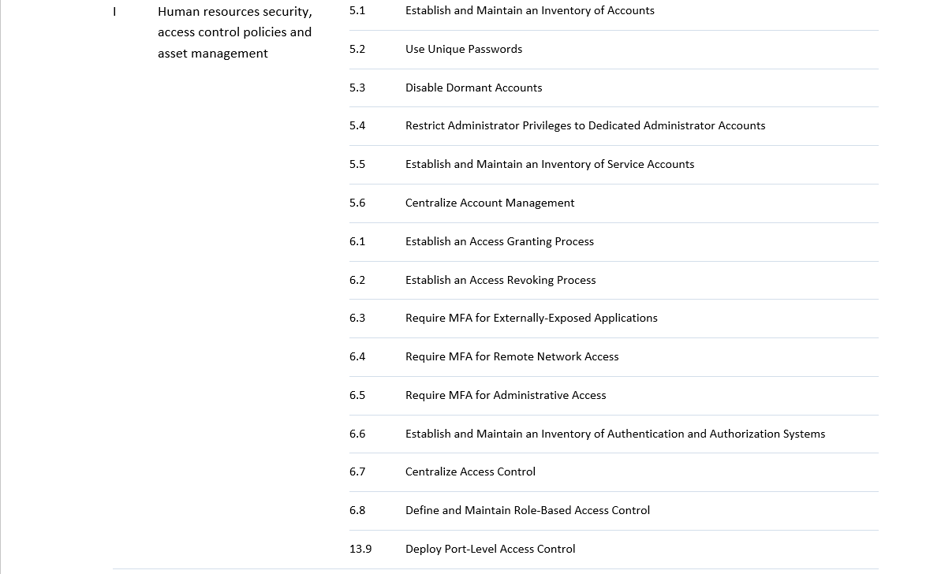
This implies a rather significant transition for most entities falling under NIS2, which can often take 1-3 years. Therefore, it is crucial that the appropriate steps are taken as soon as possible. For this, we created an easy-to-use assessment tool, mapping CIS Controls to NIS2 requirements. Although the exact requirements are not yet known, CIS controls are a valid place to start in order to gain an idea how far the company or organisation in question is in their cybersecurity processes. The tool is intended to help assess where an organisation stands in terms of relevant controls and from there to help prepare the organisation in advance to the member state adaptation. The table below maps the NIS2 measures to the CIS security controls v8.