- SERVICES
- THREATS
- Sector-based threat landscape
- Agriculture
- Energy
- Maritime
- Manufacturing
- Technology
- Logistics
- Governments
- Country threat profiles
- Russian Federation
- China
- Iran
- North Korea
- United States
- Israel
- Threat actor profiles
- Fancy Bear/APT28
- Cozy Bear/APT29
- OilRig/APT34
- Charming Kitten/APT35
- Lazarus/APT38
- Double Dragon/APT4
- Sandworm
- Seaturtle
- Silent Librarian
- RESOURCES
- ABOUT US
- CONTACT
Agriculture in the crosshairs of nation-state sponsored hackers
The global agricultural industry and the food sector are facing many challenges in the eye of growing demands due to increasing wealth and irreversible population growth. Innovations, technology and the modernization of the industry are named key elements in the securing of sufficient output on the production side. The wealthiest countries, mostly part of the global west, are frontrunners in the development of farming techniques, technology and knowledge. Other countries, often greatly dependent on their agrarian industry, do not sit back and relax while they are behind. Hunt & Hackett has observed a growing number of state-sponsored hacking groups, Advanced Persistent Threats (APTs), with varying countries of origin, that are targeting the agricultural, food and industrial industries. With espionage and information theft as their key objectives, APTs are on the hunt for all that could advance the state of their country’s agricultural sector. It is no surprise that the Netherlands, known within the international agriculture sector as the country that feeds the world, who are highly innovation driven and therefore form a prime target for a variety of state (sponsored) threat actors.
On this page, you will find what you need to know about the cyber-actors that are threatening the agricultural sector. It is described what they want, what motivates them and who they are.
“Know the enemy and know yourself; in a hundred battles you will never be in peril. When you are ignorant of the enemy, but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and yourself, you are certain in every battle to be in peril.”
- Sun Tzu, the Art of War
1. Introduction
The current global food system produces enough food to feed the entire world population. However, production is very unequally distributed, and a large share of the world population does not have access to enough food. China, Russia, USA, India and Brazil together produce over half of the world’s food supply in absolute terms. Yet, these countries have struggled to defeat malnourishment or famine within their own borders, let alone past them. This indicates the difficulty of fair food distribution. The regions of Africa and the Middle East are very dependent on food-imports, meaning that their levels of production are not meeting the growing demand. To make matters worse, in the regions where the output is already low, food production is threatened by climate change (flooding, irregular rain seasons etc.), land degradation, and lack of investments. All over the world, policymakers, farmers and researchers make tremendous efforts to increase the yields, which they have, but unfortunately far from enough to catch up with the surge in demand.
The World Food Program (WFP) has set the (over)ambitious goal of achieving zero hunger in the world by 2030. To overcome the challenges and provide enough food for the projected population of 10 billion people in the 21st century, the agricultural industry will need a drastic transformation. In many countries production is limited by outdated techniques, inefficient use of available land and the depletion of slow- or non-renewable resources. Efficiency, sustainability, and resilience can all be improved through the development of new technologies and innovations. Over the years, the sector has been moving from disconnected, independent and uncoordinated operations to highly interconnected, dependent and coordinated operations that have enhanced efficiency of both quality and quantity of yields. This is an ongoing process is also known as agriculture 4.0, which is part of industry 4.0 (see also Figure 1).
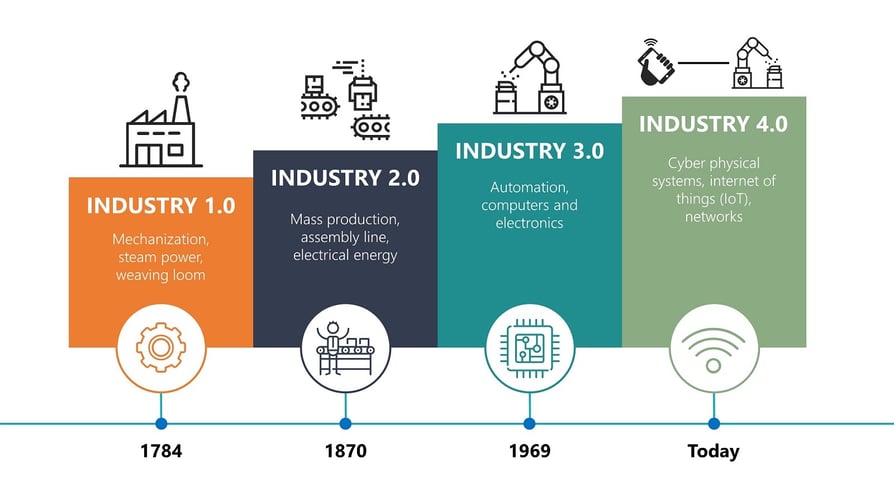
Figure 1 - The evolution of industrialization.
The inevitable transformation of the agricultural sector must happen throughout the entire food system. All cogs in the wheel, from small farming companies to massive biotech companies, are combining efforts to tackle the challenge of feeding the world while moving towards sustainability. Innovations at the smallest level can lead to substantial changes in the industry. This is also why all innovating businesses, from small farms to big agricultural enterprises, should expect unwanted attention from countries all over the world. Nation-states are aware of the interconnected nature of agriculture and will seize every opportunity to make sure they are up to speed on the latest innovations in their drive for yield growth while transitioning to agriculture 4.0. For some countries, this means complementing licit activities to gain knowhow, Intellectual Property (IP) and technology with carrying out illicit cyber operations, leveraging their APT-groups as part of the mix. Hunt & Hackett has researched the agricultural industry as a whole with all its subdivisions and related industries. This is because agriculture has a lot of overlap with (green) biotech and industrial industries. Also, as already mentioned, the rise of agriculture 4.0 is part of industry 4.0, developing and applying the same Internet of Things (IoT) and big data technologies. If the APTs active in these related industries haven’t shown activity in agriculture already, it is only a matter of time before they will.
In order to outsmart your digital adversaries, it is key to understand how they operate. Hunt & Hackett tracks their preferred attacking methods so you can build resilience against them. Hunt & Hackett has observed 111 APTs from many different countries targeting agriculture, (green) biotech and industrials. In their effort, 1574 Tactics, Techniques & Procedures (TTPs) and 1442 Tools have been used. It is vital to understand that these are known observations. Many cyber-attacks are not being reported or made public, rendering the actual numbers of Tools and TTPs much higher.
| APTs | TTPs | Tools | |
| Agriculture, Biotech & Industrials | 111 | 1574 | 1442 |
| Biotech | 57 | 921 | 865 |
| Agriculture | 19 | 371 | 354 |
2. Challenges
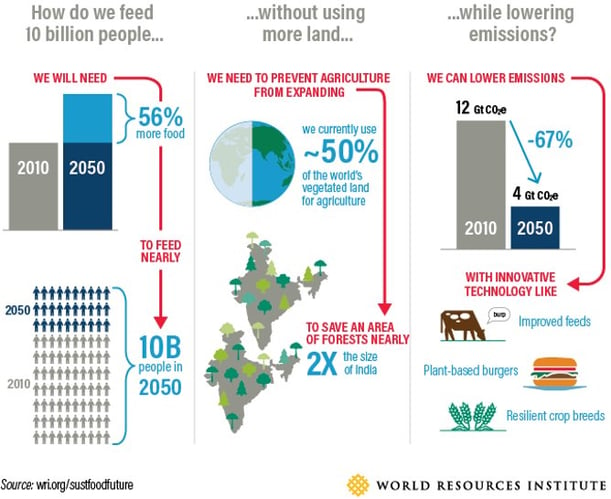
Figure 2 – The challenges for the global agricultural industry.
To meet the increased demands, farming has evolved to a stadium long past the one of hitching an ox onto your plow and hoping you harvest enough crops to make some money at the local market. Nowadays, the food system is a global interconnected industry using genetically modified seeds and state-of-the-art automated technologies to secure the biggest yields and use the available land as efficiently as possible. The food supply chain is highly concentrated with a limited number of organizations controlling the global market. Innovation by the leading organizations is widely regarded as potential solution for the rising demand while dealing with the devastating impact of climate change and resource scarcity. Through academic and research partnerships, mergers and acquisitions, and other ways of cooperation between countries, knowledge gets the chance to spread around the world. However, for some states this overt cooperation is too slow, too costly or simply not a viable option. They prefer or complement their licit activities with an illicit way of obtaining information and technology: cyber-attacks.
"There are now three certainties in life - there's death, there's taxes and there's a foreign intelligence service on your system."
- Sir Iain Lobban, Former Director GCHQ
Information and technologies that could help nations in providing food security for their population is badly wanted. Through cyber espionage, expensive and time absorbing R&D projects are being avoided while the risk of getting caught or facing lasting consequences is low. Through their own, sponsored, affiliated or tolerated APT-groups, governments can deploy highly sophisticated cyber-attacks anywhere in the world from a safe distance. This distance is not just physical, governments often deny any kind of connection to the affairs of these APTs. By doing so, it is difficult for the international community to punish or blame governments for the cunning cyber-attacks of their APTs, even though little question exists about their actual involvement.
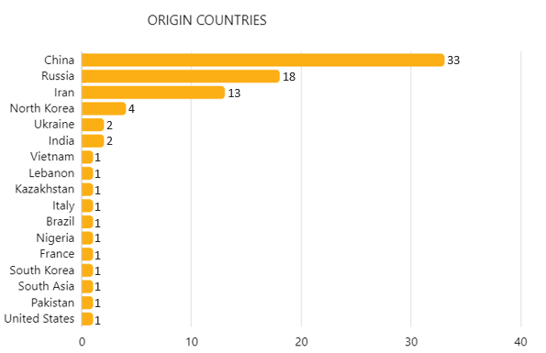
Figure 3 - Origin countries of APTs active in agricultural and related industries as observed by Hunt & Hackett (only 17 are displayed here)1.
There are many countries known to make use of APTs extensively, even Western allies like the UK, France and the US sometimes attacks friendly nations. However, in the agricultural sector and related industries, most cyber-attacks are being commissioned by the usual suspects: China, Iran, Russia and North Korea (see also Figure 3). Using their extensive cyber capabilities has become an integral part of their strategy to further develop their economy. Where some countries, like the Netherlands, focus on defensive cybersecurity, other countries have already set up offensive cyber-capabilities and use them for economic espionage. In the next parts of the series, we will look into why these countries in particular stand out in their use of APTs in the agricultural sector and what activity has been observed in the past.
3. Most active countries
China
The Democratic Republic of China is well underway of becoming the global hegemon, challenging the United States who currently hold this position. To succeed in its catch-up, China has active policy in place to acquire foreign technology and know-how. The policy consists of a multifaced plan that is meant to perform an upgrade to China’s economy and overall power. Modernizing the agricultural industry is a vital part of the plan. Feeding 1.4 billion people is not an easy task, given the fact China has only a relatively low percentage of land fit for agriculture and is facing increasing desertification and deforestation, further reducing their amount of agriculture land. Western technology and knowledge would surely increase the resilience of the Chinese food system and the efficiency of their farming practices.
China has many partnerships, regulatory strategies and corporate practices in place to overcome the innovation gap between them and the global West. Although a lot of information is exchanged, Western states and companies are not quite eager to share their most valued secrets, as one can imagine. In order to acquire precisely these kinds of secrets, the Chinese government has a known record of deploying their vast cyber apparatus. The Chinese APTs carry out numerous attacks all around the globe. In the agricultural industry, espionage and information theft have been singled out as their main motives. This illustrates clearly that APTs are being used to support China’s modernization efforts and play an important role in achieving its strategic goals (see also figure 4).
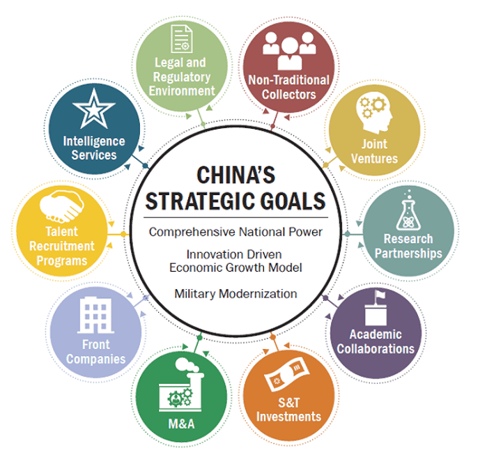
Figure 4 - China's multipronged approach to its innovation driven economic growth model.
An example of a Chinese APT active in agricultural and industrial sectors is APT 41, also known as WICKED PANDA. This hacker group, which has also been observed in the Netherlands2, became known to the public after they hacked Bayer, the largest agricultural supply company in the world. Bayer claims that they have found no evidence of information theft, fortunately3.
Hunt & Hackett outsmarts hostile APTs by tracking and anticipating their preferred attacking methods (TTPs) and the Tools they use. Hunt & Hackett is aware of 33 APT-groups, which have been attributed to China, which are targeting agriculture or related industries now and in the past. Do note that some of them aren't active anymore, or at least have not been noticed by other security vendors in the past couple of years. Of these 33 APT-groups, 489 TTPs and 490 Tools leveraged by Chinese APTs are known to Hunt & Hackett.
| Key Stats China: Agriculture and Related Industries | |
| APTs | 33 |
| Names of APTs | APT1; APT10; APT15; APT17; APT18; APT19; APT20; APT23; APT26; APT27; APT3; APT40; APT41; APT5; BlackTech; Blue Termite; DragonOK; Ice Fog; etc. |
| Level of Sophistication | High |
| Main Motives | Information Theft; Espionage |
| TTPs | 489 |
| Tools | 490 |
Table 2 - Key statistics on APTs originating from China, and the TTPs and Tools they use in the agricultural and related industries as observed by Hunt & Hackett1.
Russia
In the aftermath of the downfall of the USSR, Russia fell into chaos transforming from a state led market to an open and free economy. The first ten years, there was hardly any progress if not a set-back. Under President Putin, order was restored, and efforts to modernize the former leading Soviet nation could begin. For the agricultural sector, this was and still is a difficult task, given the fact that heavy industry had been prioritized over agriculture for the greater part of the 20th century.
That Russia is moving up the agricultural industry on their agenda is illustrated by several Food Security strategies being released in the last ten years. In the strategy documents, it is underlined that Russia needs to move towards self-sufficiency and away from dependency of other nations. It is also discussed how Russia’s food industry should cope with the threat of enduring international sanctions by stimulating the domestic (bio)technology- and scientific sector4.
Russia has never shied away from using illicit methods for the nation’s economic benefit. Not in the past, not in the present and not in the future. Making use of their highly skilled and sophisticated APTs in support of modernization efforts has been a key part of Russia’s strategic planning. Shopping abroad what you lack domestically seems to be the motto of Russia’s modernization strategy. This was also the conclusion of the Dutch general intelligence service, the AIVD, as they wrote in their 2020 yearly report5. In terms of activity, Russia is not the most dangerous adversary. In terms of quality, however, there are few countries that can trump Russian offensive cyber skills.
A very recent example of Russian cyber-aggression was a Russian APT exploiting a vulnerability in popular and widely used software by the American company SolarWinds. The state-backed hackers hid a backdoor in an update package, so when users would update their software the Russian gained access. By doing so, Russian state-backed hackers could access the systems of around 18.000 SolarWinds clients (see also figure 5).
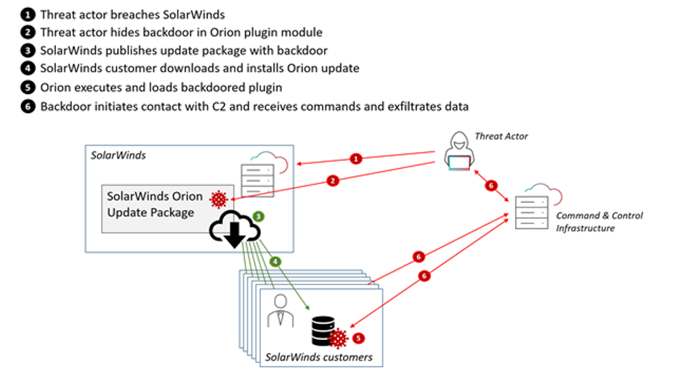
Figure 5 - How the Solarwinds hack took place.
A total of 18 Russian APT-groups (now and in the past) that have been active in agriculture or related industries are known to Hunt & Hackett. To counter and to be prepared for their cyber-attacks in the future, Hunt & Hackett tracks the TTPs and Tools they have employed in the past. At this moment, Hunt & Hackett has encountered 423 TTPs and 339 Tools used by Russian APTs in the relevant industries.
| Key Stats Russia: Agriculture and Related Industries | |
| APTs | 18 |
| Names of APTs | Anunak; APT28; APT29; ELECTRUM; Hades; Inception Framework; INDRIK SPIDER; OldGremlin; Operation BugDrop; TA505; TeamSpy Crew; TEMP.Veles; Turla Group; UNC1878; Union Spider; VENOM SPIDER; etc. |
| Level of Sophistication | High |
| Main Motives | Information Theft; Financial Gain; Espionage |
| TTPs | 423 |
| Tools | 339 |
Table 3 - Key statistics on APTs originating from Russia, and the TTPs and Tools they use in the agricultural and related industries as observed by Hunt & Hackett1.
Iran

| Key Stats Iran: Agriculture and Related Industries | |
| APTs | 13 |
|
APT Names |
APT33; APT35; APT39; Boss Spider; Cutting Kitten; Fox Kitten; Infy; ITG18; Madi; MuddyWater; Nazar; Sima; Tortoiseshell |
| Level of Sophistication | Medium |
| Main Motives | Espionage; Information Theft |
| TTPs | 168 |
| Tools | 158 |
Table 4 - Key statistics on APTs originating from Iran, and the TTPs and Tools they use in the agricultural and related industries as observed by Hunt & Hackett1.
North Korea
The North Korean regime is going to have to use every resource available to increase yields and modernize their agricultural sector, in order to provide structural food security for the population. Not known to many is that the regime has very capable APTs at their disposal which it is not reluctant to deploy10. North Korea is known to have used APTs to steal secrets and technology from all over the world. North Korean hacker groups SILENT CHOLLIMA and LABYRINTH CHOLLIMA, have been observed to target the agricultural industry, as became apparent in June 2020, when an American company active in the agricultural industry fell victim to the latter APT11. It is assessed that North Korean’s world wide presence will increase because of the mounting pressure of another famine. A sign of their increasing sophistication is that North Korean hackers have already figured out how to overcome the ‘air-gap’, meaning that they have the ability to hack computers not connected to the internet12. Previously, this was a skill only more technological sophisticated nations mastered.
Figure 7: Under Kim Jong-Un, North Korea has developed a very capable cyber force.
To deal with the North Korean cyber-threat, it is important to understand how their APTs operate. This is the reason Hunt & Hackett has tracked the TTPs and Tools the have employed in the past. Hunt & Hackett has observed 4 North Korean APT-groups to be active in agriculture or related industries using 133 TTPs and 217 Tools.
| Key Stats North Korea: Agriculture and Related Industries | |
| APTs | 4 |
| APT Names | APT37; APT38; Kimsuky; Wassonite |
| Level of Sophistication | High |
| Main Motives | Espionage; Information Theft |
| TTPs | 133 |
| Tools | 217 |
Table 5 - Key statistics on APTs originating from North Korea, and the TTPs and Tools they use in the agricultural and related industries as observed by Hunt & Hackett1.
4. Spying on the Netherlands
The Netherlands is an obvious target for countries who are seeking to upgrade and modernize their agricultural sector. The Netherlands is world-renowned for its innovative industries and high-quality products. The agricultural sector is a shining example. An export value of over €95 billion was realized in 2020 and is expected to grow over the next few years. The Dutch industry has a broad scope of expertise, ranging from turn-key greenhouse farming concepts to genetic modification of seeds. This expertise is the result of many years of cooperation between the government, farming companies and researchers. Through a focus on research and development, with companies often investing up to 40% of revenue back into R&D, the Netherlands has built up to an excellent information position in the global agricultural industry.

Figure 8 - The Netherlands is one of the leading nations in agricultural innovations.
It is not all puppies and sunshine for the Dutchies, however. The agricultural sector is also responsible for a large part of the country’s emissions of, not so ironic, greenhouse gasses. The industry has to undergo a major transformation to ensure a sustainable future. The Dutch government is planning on investing heavily in the sustainability of the industry. The imminent transformation to agriculture 4.0 means that yet again a lot of research and development has to happen. The insights of these costly processes could save other nations, such as China, a lot of time and effort if they were to get their hands on it. The know-how and advanced technologies the Dutch use in their greenhouses, on their fields and in their labs are a potential goldmine for countries struggling with their own food security or seeking to modernize their economy.
The tight cooperation between the government, universities and farming companies gives attackers a wide attack surface to achieve their goals. At all levels, everyone that is involved in the development, manufacturing or deployment of agricultural innovations should be aware of the extra sets of eyes lurking in the dark, trying to find a way in. Espionage and information theft have never been a more viable option than today. There is no need for on scene action by heroic James Bond-like figures; a few tech-savvy millennials can deliver much more to their governments from their offices in Beijing, Moscow, Tehran or Pyongyang.
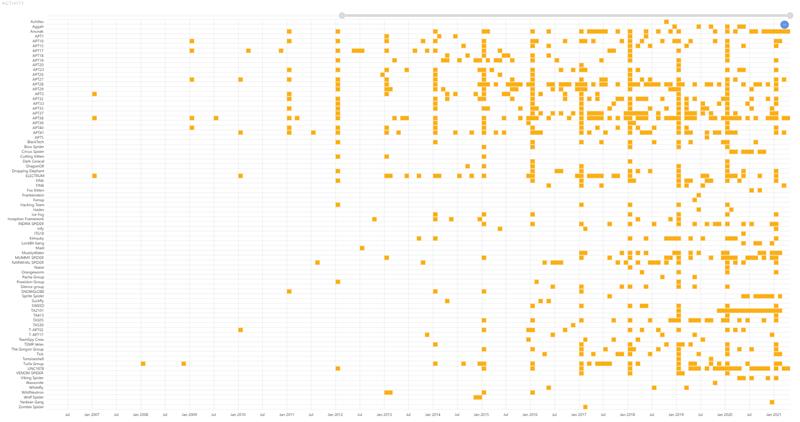
Figure 9 - Hunt & Hackett has observed a sharp increase in APT activity in agriculture and related industries1.
In this series of blogs by Hunt & Hackett on the increasing threat (see figure 9) of nation-state sponsored APTs for the global and Dutch agricultural industry, we have elaborated on who the attackers are, what they want and why they are using offensive cyber capabilities to meet their goals. Hunt & Hackett is actively hunting for the APT-groups that threaten the agricultural industry. APTs rely heavily on the Tools and attacking methods they are acquainted with. By tracking the TTPs and Tools these APTs have used in the past, Hunt & Hackett takes the power of their weapons away and is prepared for their future attacks. This adversary central approach is known in cyber-security as Threat Modelling and enables organizations to defeat their opponents time and time again.
5. Sources
- All data used in tables and in figure 3 and figure 9: Hunt & Hackett Threat Diagnostic Tool.
- https://apt.thaicert.or.th/cgi-bin/showcard.cgi?g=APT%2041&n=1
- https://www.cyberscoop.com/bayer-breached-china-wicked-panda/
- https://apps.fas.usda.gov/newgainapi/api/Report/DownloadReportByFileName?fileName=New%20Food%20Security%20Doctrine%20Adopted_Moscow_Russian%20Federation_02-03-2020;
- https://www.aivd.nl/binaries/aivd_nl/documenten/jaarverslagen/2021/04/29/aivd-jaarverslag-2020/AIVD-jaarverslag+2020.pdf
- https://www.worldbank.org/en/country/iran/overview
- https://smallwarsjournal.com/jrnl/art/islamic-republic-irans-strategic-culture-and-national-security-analysis
- https://www.recordedfuture.com/iran-hacker-hierarchy/
- https://securityboulevard.com/2021/04/analysis-of-the-iranian-cyber-attack-landscape/
- https://www.crowdstrike.com/blog/how-threat-hunting-uncovered-attacks-in-the-agriculture-industry/
- https://www.access42.nl/wp-content/uploads/2020/09/Overwatch-Report-2020.pdf
- https://www.nbcnews.com/news/north-korea/watch-out-north-korea-keeps-getting-better-hacking-n849381