Responding to Ransomware
Crisis Workshop | May 23 | FULL
Unfortunately, this workshop is full. Still interested? Subscribe to our Responding to Ransomware workshop on June 20.
In 2024, the dangers of ransomware are widely acknowledged. But despite increased awareness, many organizations still find themselves unequipped to deal with this threat due to a lack of experience and training. During a ransomware attack, critical decisions must be made quickly, leaving minimal room for error. Multiple stakeholders must work together to minimize the impact and restore operations, while dealing with external pressure from customers, partners and regulators.
During this 'choose your own adventure' workshop, you will experience a ransomware attack through the eyes of several key stakeholders. The choices you make will steer the course of the session, and the implications will be revealed as the story progresses.
What you’ll gain:
- Actionable advice for stakeholder management
- Insights into ransom negotiation and payment
- Increased awareness of the legal and regulatory implications
- The chance to connect with industry colleagues and security experts
Who should attend?
- CISOs, IT Directors, and IT Managers
- CEOs and CFOs
Please note that places for this workshop are limited. Sign up on this page to secure your spot!
Practical Information
- When:
Thursday, May 23
15:30 - 18:00 - Where:
Hunt & Hackett's office
New Babylon
Anna van Buerenplein 46
The Hague
Find on Google Maps
Programme
- 15:00 – 15:30
Arrival - 15:30 – 17:30
Hunt & Hackett's security experts will guide you through the process of responding to a ransomware attack, highlighting critical decision points along the way. Our team has accumulated a wealth of experience on this topic, having participated in many high-profile ransomware investigations. - 17:30 – 18:00
We will conclude with some key takeaways and actionable recommendations that you can take back to your own organisation. - 18:00
Borrel.
Ransomware in 2024
The Definitive Guide
Ransomware is defined as "a type of malicious software designed to block access to a computer system until a sum of money is paid." In general, ransomware can be distributed randomly or in a (semi-)targeted manner. The latter can be aimed at either individuals, or to specific businesses, organisations, or government agencies. Ransomware attacks, and targeted ransomware in particular, can result in serious consequences for the victim, such as the disruption of operations, financial loss, or the loss of sensitive or proprietary information. The motivations behind these attacks vary, but most often the attackers are seeking to extract a large sum of money from the victim. In some cases, the attackers may also be motivated by political or ideological goals, such as causing disruption or destruction.
Ransomware Actors
Ransomware actors come in all shapes and sizes. They can be well-organized and even state-funded Advanced Persistent Threat (APT) groups, politically or socially motivated hacktivist teams, or even bored individuals with questionable moral standards looking to stir chaos and gain financial advances. Some of them focus primarily on ransomware attacks, while others specialize in, say, espionage, but occasionally engage in ransomware attacks. Hunt & Hackett currently tracks 97 distinct ransomware actors.
When a ransomware attack takes place, it is not always obvious who is behind it. Often times, attacks and the malware used remain unattributed to any specific known or emerging group. Based on the available information Hunt & Hackett has compiled, Russia, China and Iran have the highest number of groups operating in the business of ransomware. Even though their main targeted countries vary, and social and political events often change the dynamics, in general the United States, the United Kingdom and Germany experience the highest number of attacks.
A Typical Ransomware Attack
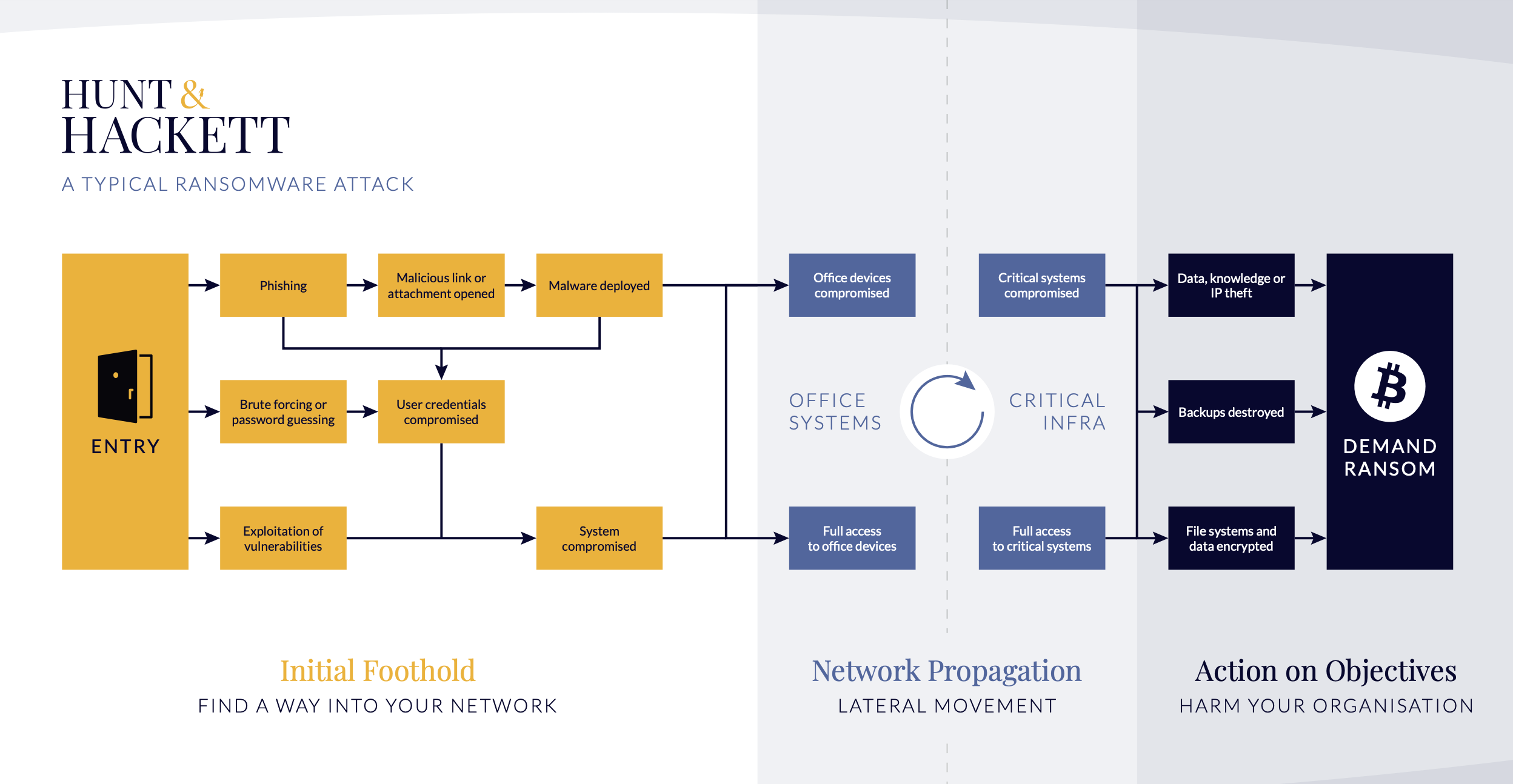
Groups that have been observed to engage in ransomware attacks tend to use a wide variety of techniques, but Phishing, using Command and Scripting Interpreters, Obfuscating Files or Information, enticing User Execution and using Encrypted Channels are among the most utilized methods. The picture above shows the phases of a typical ransomware attack. This includes the initial foothold phase, during which the attackers gain access to the targeted network and start establishing their presence. During the next phase, network propagation, the attackers gain access to more devices or even the whole infrastructure. The last phase – action on objectives – is what is commonly thought of as the attack itself. This is when the attackers conduct the actual information theft, encryption of files, destruction, or all of the above. These moves then allow them to demand ransom from the organization in exchange for the stolen or encrypted data. However, it is worth noting that this is only one way of conducting a ransomware attack, and more variations have been continuously emerging. For instance, triple extortion attacks would involve additional steps, most often DDoS attacks and publication of stolen data. The following section will explore the different variations to better understand how ransomware attacks can play out.
Interested in learning more? Read our definitive guide to ransomware at the link below.